Brazil.. Haven for Botnet's and C&C servers?
I have been running HoneyPot's on and off for a few years, but recently have put one up permanently the last few months for more intel and for public use, learning and entertainment. You can see statistics and live attacks on the Live HoneyPot dashboard links page below.

I am always fascinated by this constant activity, as without fail, any honeypot I put up on a new IP on any host, within 24hrs starts to get blasted. The DDOSPOT specific Pot attacks specifically are continual and non stop. When I mean blasted, I am talking about 2.5 million logged DDOSPOT attacks in a matter of a couple weeks. This isn't even mentioning the other Pot sub-type attacks.
In fact, a couple times, the HoneyPot got so overloaded, the server could not keep up with the logging and activity. Which a few times freezes the Pot. I have only had to reboot the Honeypot a handful a times over months. Only during the heaviest barrage is this necessary. This is a 8vcpu server with 32GB RAM with SSD storage, no slouch in terms of running a honeypot.
DigitalOcean, my current provider for the Pot, has been great about this. The first few HoneyPot's I hosted, they clearly let me know it had high activity. After I explained the goal and purpose of the HoneyPot, they have been really cool and whitelisted any further automated monitoring alerts in the name of Cybersecurity research and learning purposes.
The attack origin is completely disproportionate in the sense that Brazil seems to have the most compromised devices involved in various Botnet's and malicious activity. Which is why I always block via GEO/IP Brazil on all firewalls and security layers we put in place. It is not a perfect solution, but for some reason, it has always fascinated me that Brazil always has BY FAR the most attacks by origin within any honeypot I run, regardless of configuration and location.
People always ask, when I add Brazil to GEO/IP filters by default. Isn't Russia, China and Vietnam the typical countries where typical malicious cyber activity originates from? We all seem a little intrigued when Brazil is mentioned in the list of the Big 10. I guess we are all stereotypical when we envision Brazil as a warm, friendly country with beaches and the like.
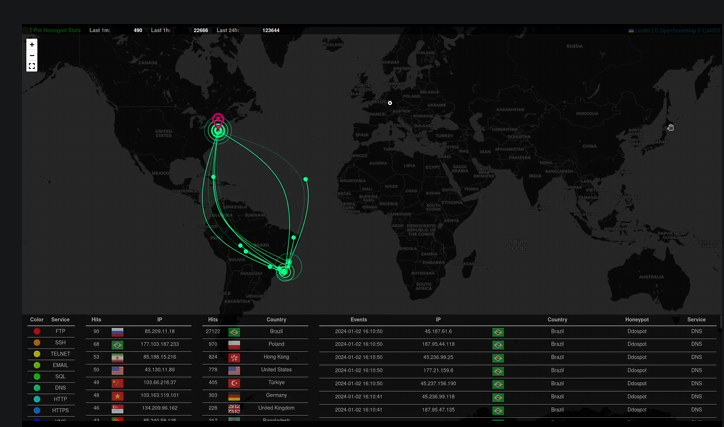
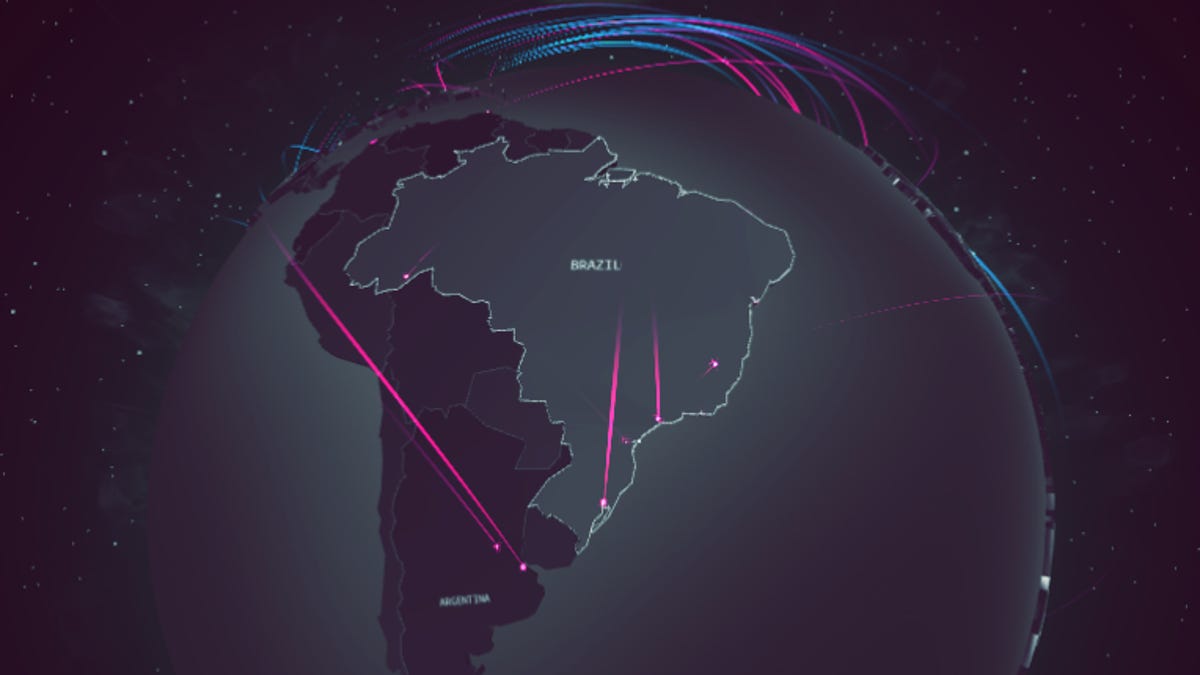
Below is a typical screenshot of the constant ongoing scanning, brute force and botnet activity our HoneyPot's experience nonstop. These are without fail always originating from the south east portion of the country of Brazil.
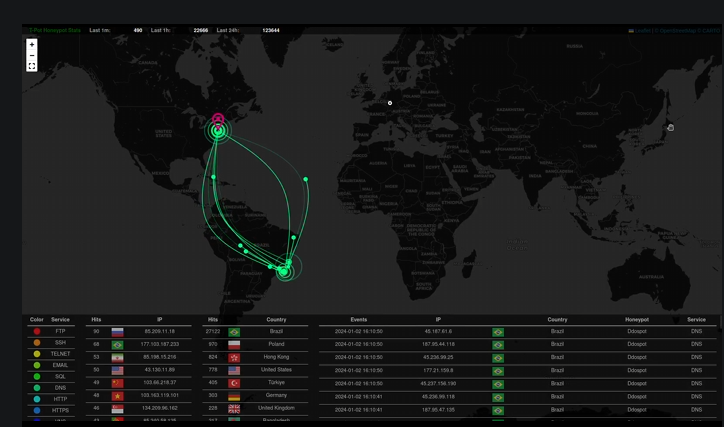
Like I said, the attacks are always out of the same location in the South East corner of the country. So I dug into OpenCTI and searched for activity in Brazil, where many cities IP's are geo-located in this area. For some odd reason the attack maps and data always seems to show the South East corner of the Country.
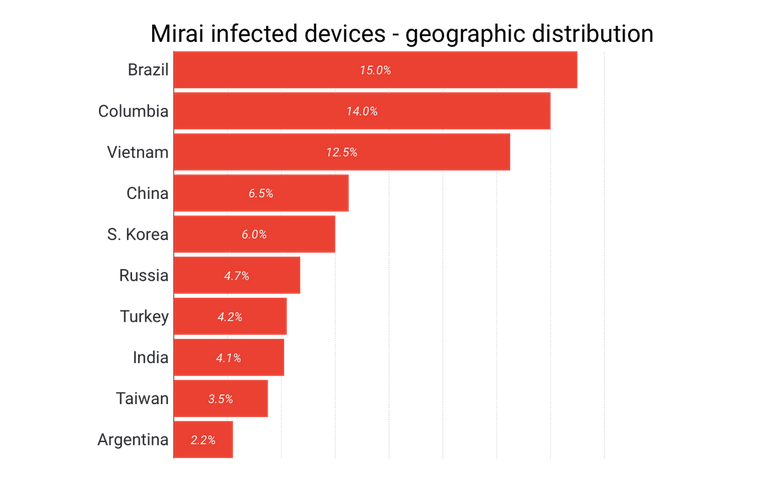
Brian Krebs released data that also matches our OpenCTI data and our HoneyPot data. This is in the context of the most infected number of hosts by country for the Mirai Botnet for example.
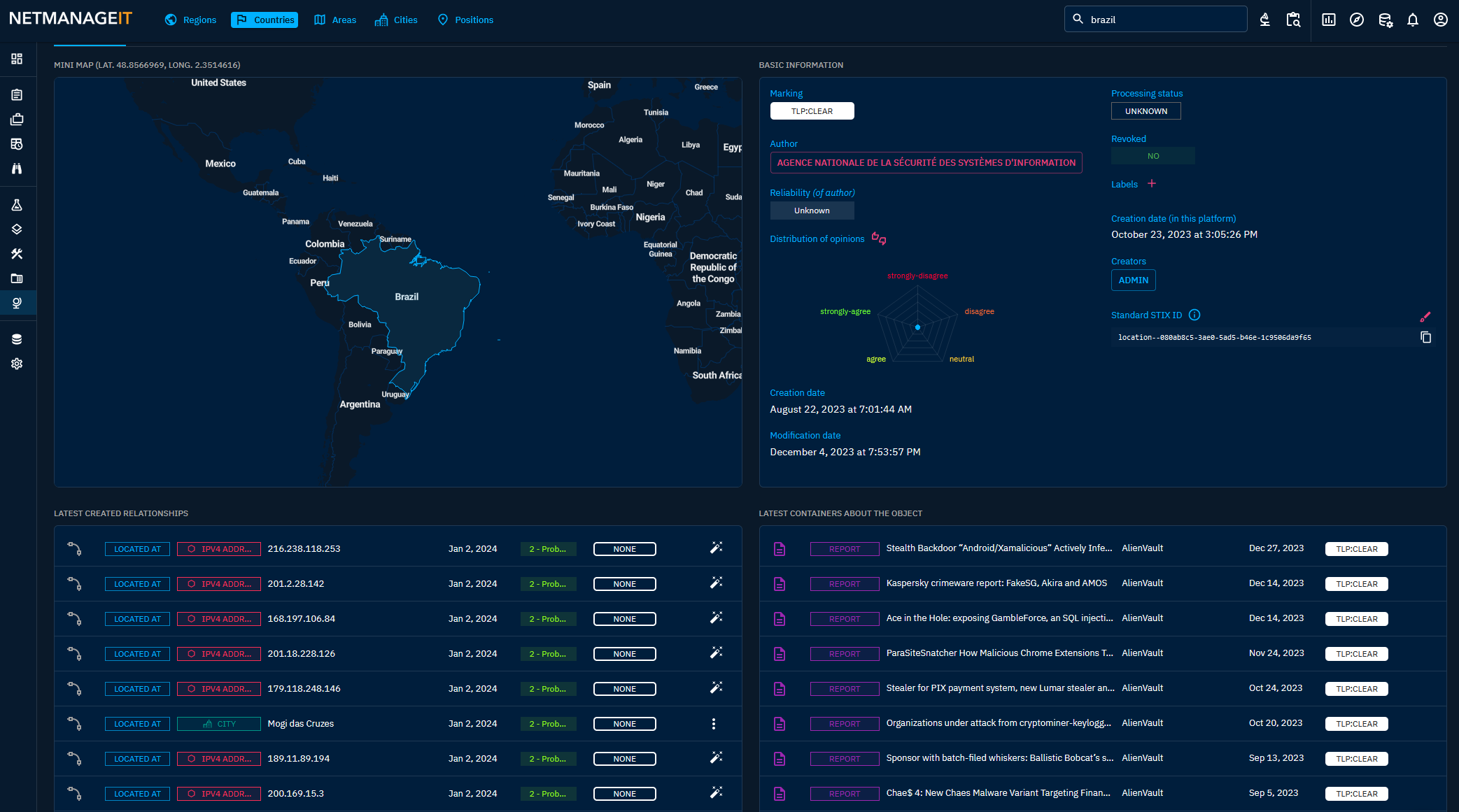
Here are some additional screenshots of Observables and Activity for Brazil and the region from OpenCTI, and there are plenty!
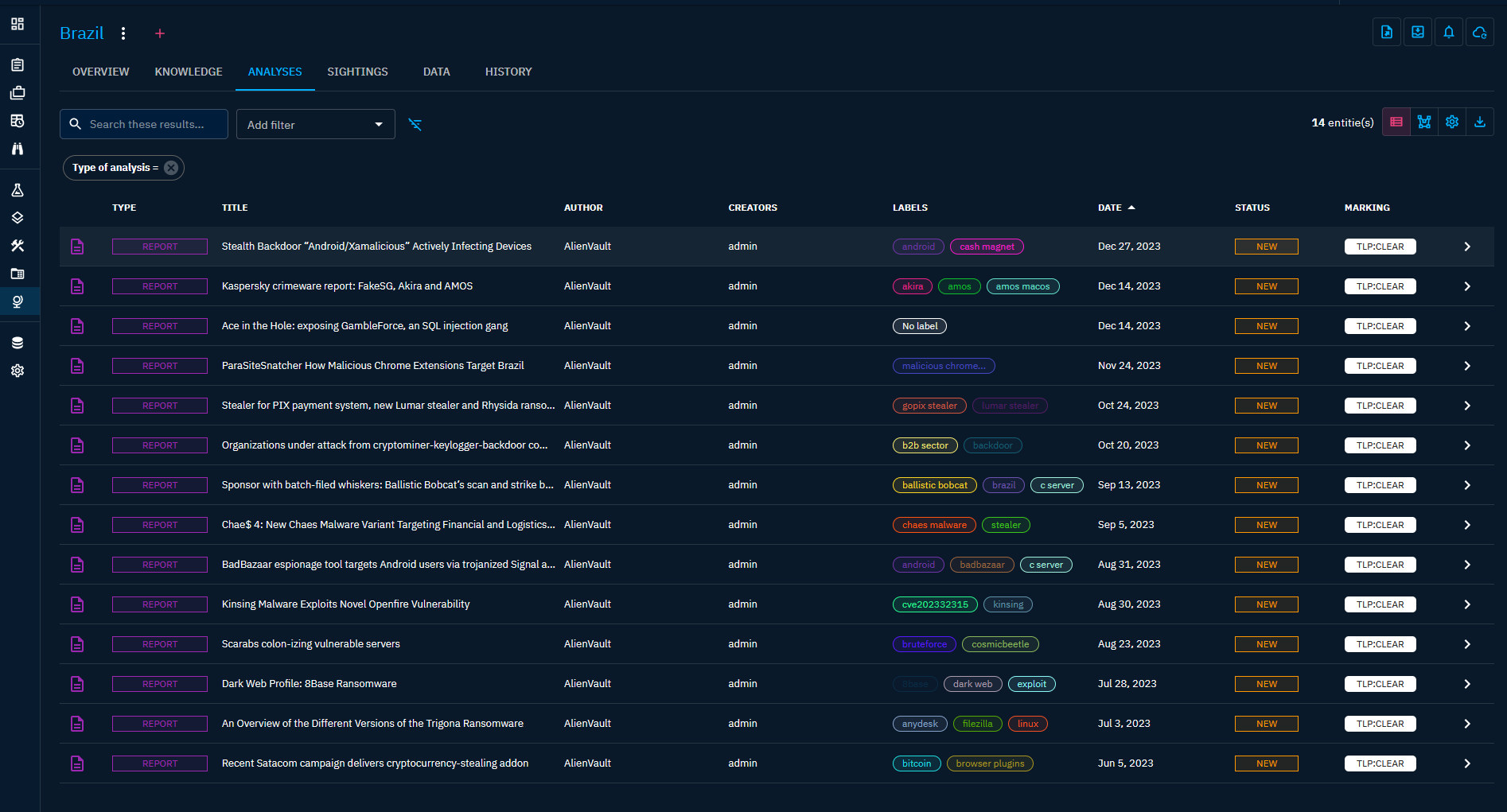
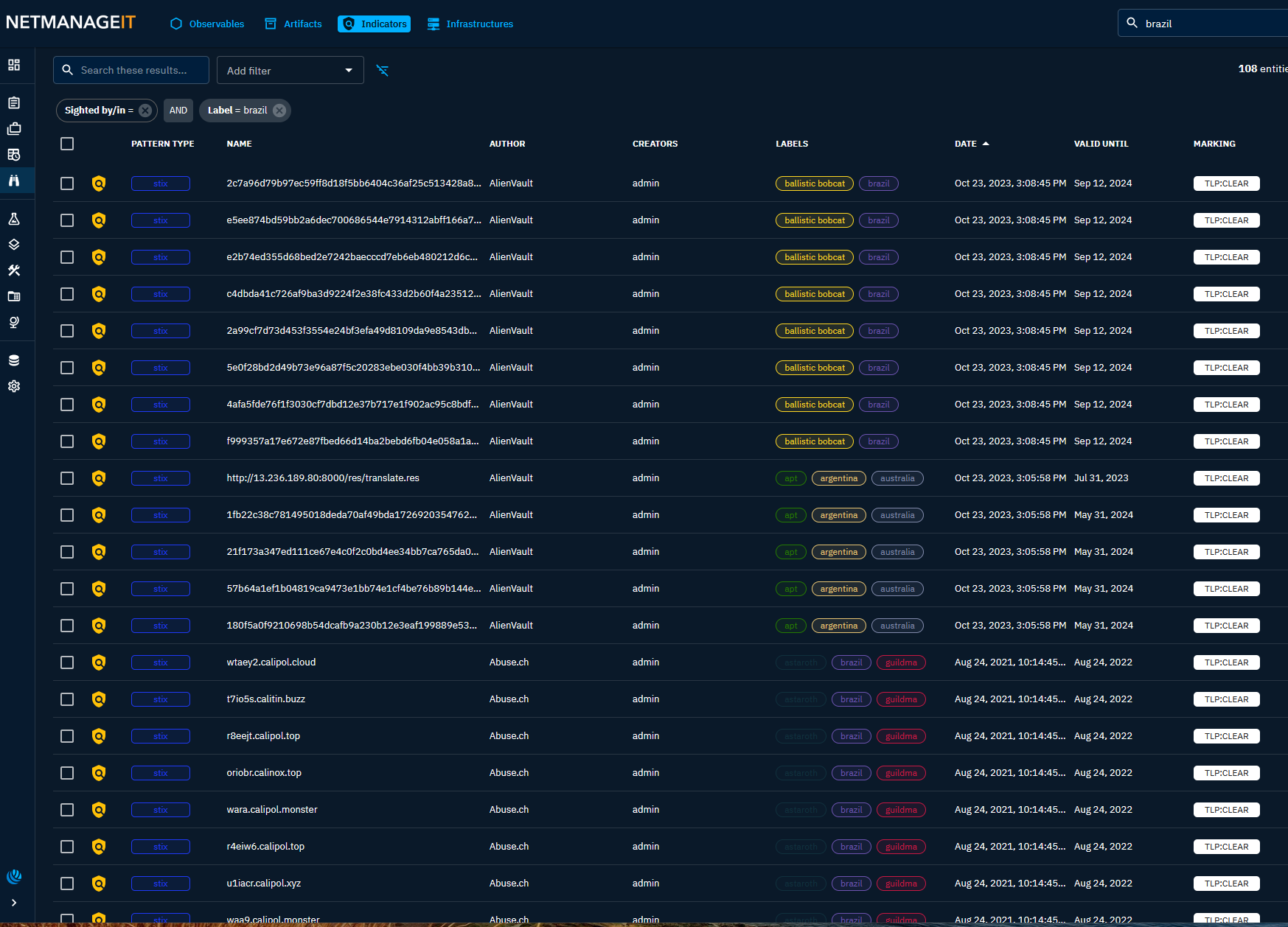
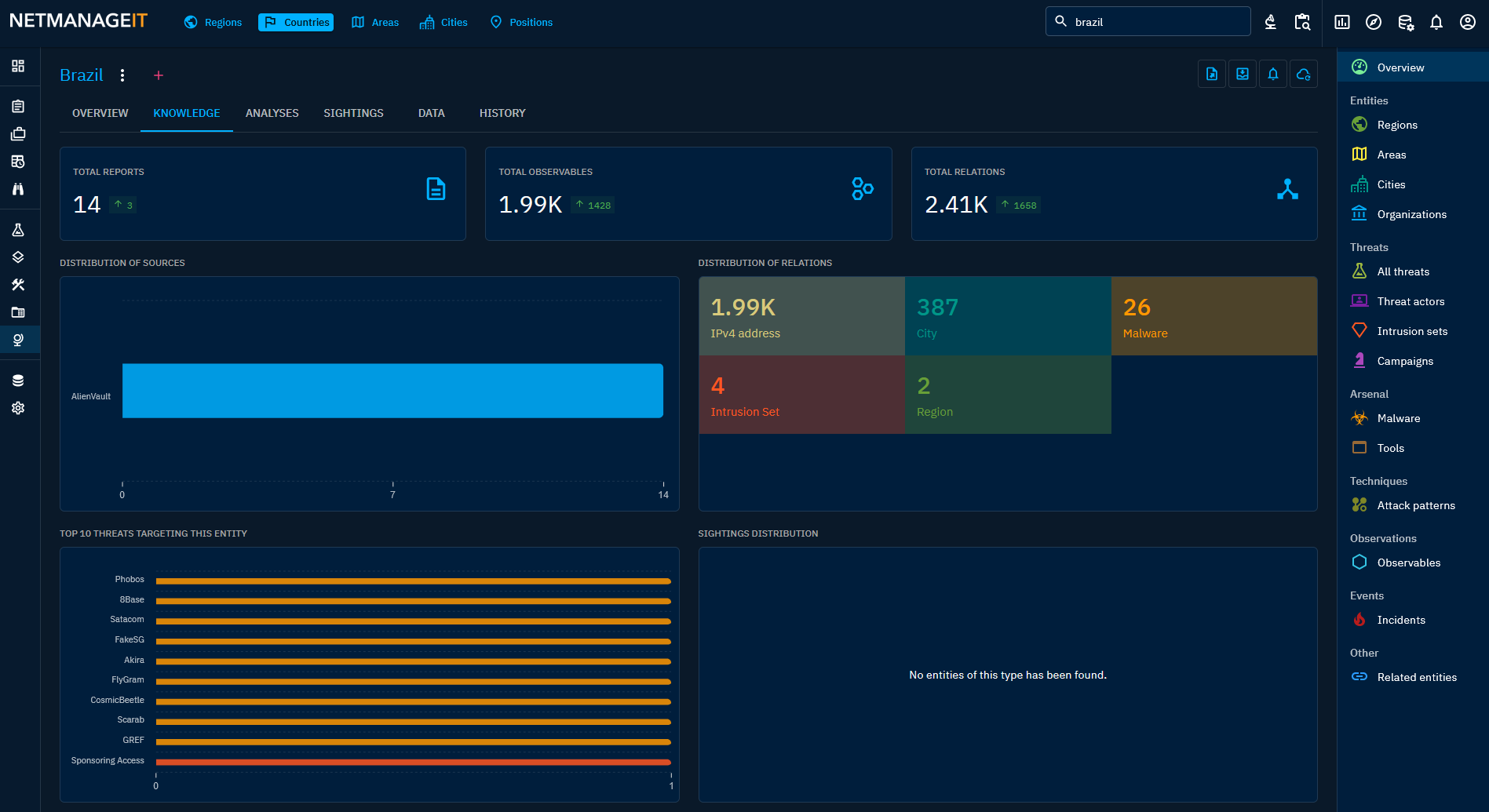
I also found multiple articles all reporting on similar findings. So this blog post is more out curiosity and intrigue, and poses a question. Why is Brazil such an easy target to take over devices and infect with malware? Here are a few articles that might shed some further insights on that question. Seems like IOT devices and Brazilian routers are a favorite among other scams that target Brazilians. As well as why our attack map is constantly lit up from attacks from Brazil.
/cdn.vox-cdn.com/uploads/chorus_asset/file/10793345/acastro_180507_1777_microsoft_0001.jpg)

If you have any thoughts or comments, see my LinkedIN post referencing this article below.

LinkedIn Post Discussion
As always, if you want to do your own research or play around with OpenCTI, be sure to visit our Public OpenCTI instance:
https://opencti.netmanageit.com
I feel as though sometimes, Brazil / China Botnet is trying to take down the Pot, but they haven't succeeded yet. :)
God Bless
Dan









