Wazuh. Detecting Malicious activity on web/cloud servers.

This is not a full howto, more of a quick demonstration of how Wazuh can put eyes on your web server's, cloud services etc. In my case, I got a few email alerts of level 12 and above wazuh alerts in regards to my Blog Server.
We have been using Wazuh in production now for well over 2 years at our MSP as an additional add-on / standard part of our security stack. It pairs nice with any modern NGAV/EDR protection. It has a lightweight footprint, and can really fill in some holes and check those compliance boxes. That being said, I want to make this fairly short. I've debated doing a full Wazuh Install/Use HowTo for a while now, but I haven't. There are a few reasons for this.
Its much easier to install and use than OpenCTI for example, which is why I have focused more on that platform. Second, everybody is talking about it lately, and have gotten on the bandwagon as they should be! It is an awesome, powerful platform, and for free?? Its hard to even believe something this good, and innovative can be installed for free and used and configured in so many ways, its very powerful. In our case, we have just around 1000 endpoints configured, and growing rapidly. Since its no cost, other than setup of the back end, and the knowledge to configure it and customize it. I'll leave that discussion and conversation for another time.
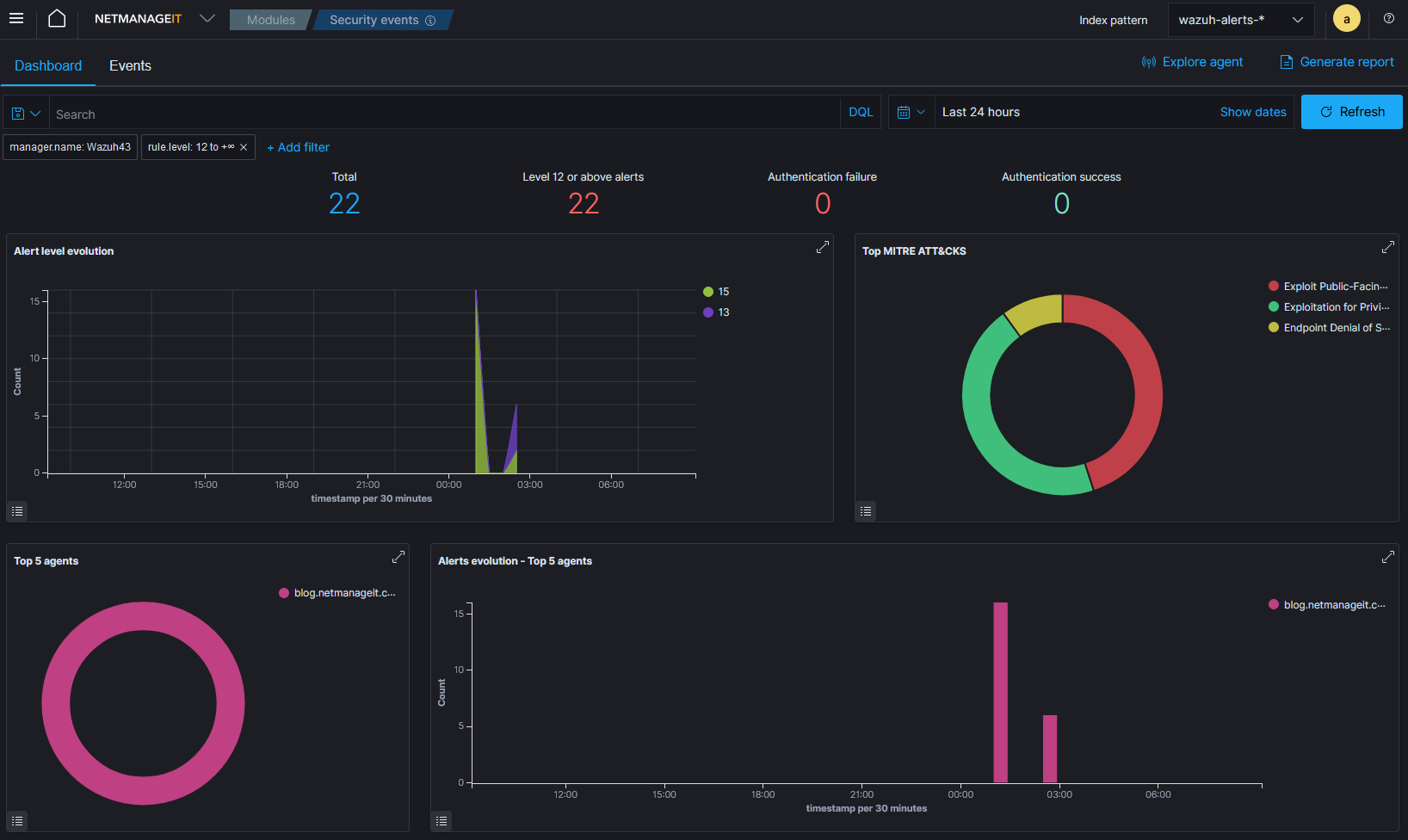
Getting back to the main point of this blog. So after getting email alerts of these alerts, I went into the Wazuh dashboard and clicked on "security events". From there, clicked on my Level 12 or above Alerts option up top. This tells us of any fairly critical things we should be looking at. In this case, middle of the night numerous events logged clearly showing probing, scanning and exploitation attempts.
You can see in the screenshots the events, such as ShellShock attack, often caused by tools like Zgrab2 Scanner, OpenVAS, Nikto scanners etc. which are looking for vulnerabilities of a target. It run's through a bunch of tests, and these are standard checks. Also notice the alert for a malformed http request, very long string.
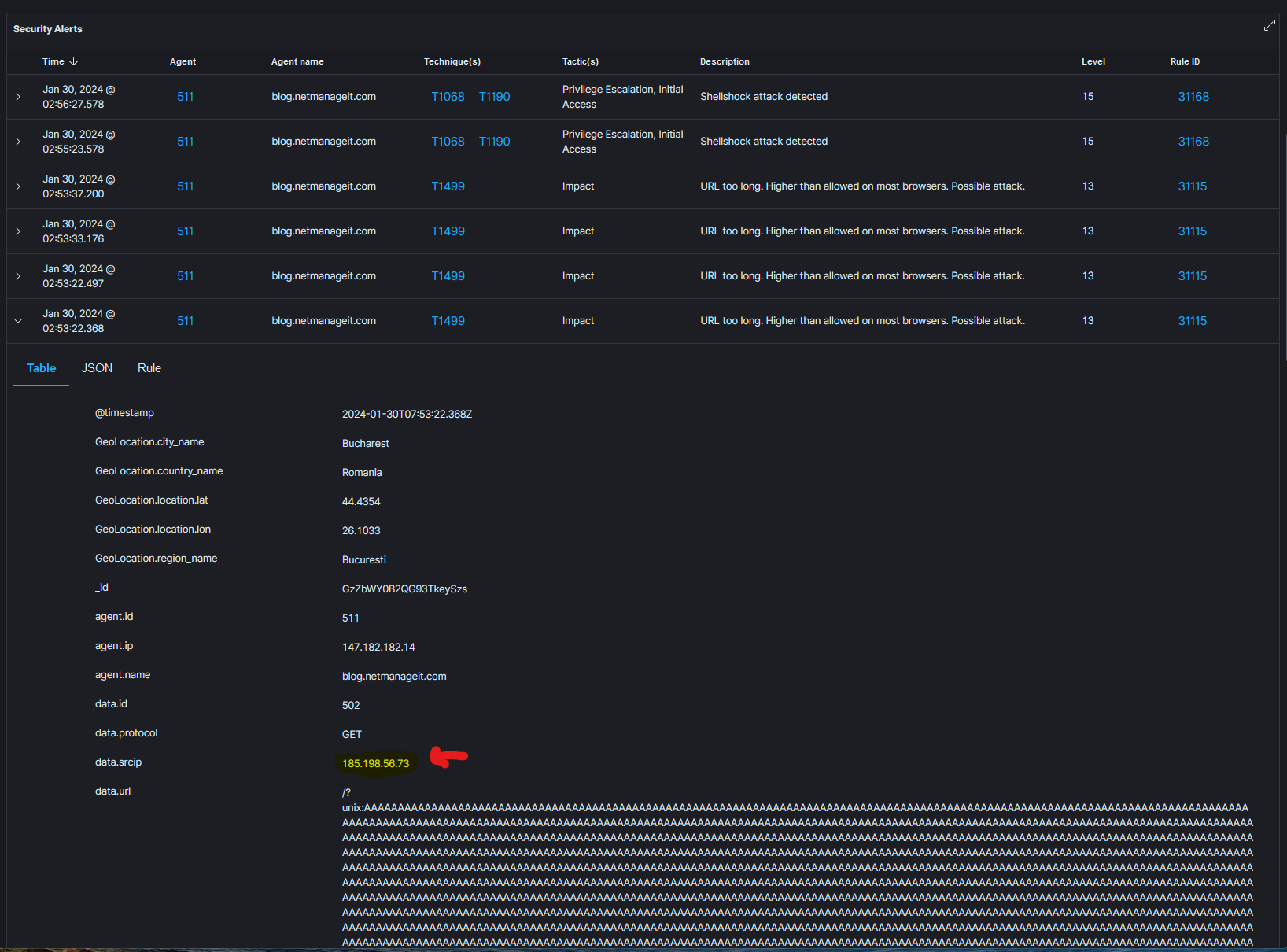
So this happens all the time, you may just not know about it if your not monitoring things, or have these types of tools in place to give you full visibility. Nothing to worry about. As I know my server is patched up to date, Ghost platform up to date, and all security practices followed down to the HTTP security headers setup optimally. Not to mention I regularly scan our sites personally with the same tools hackers are using. If something is found, its fixed immediately.
Interesting enough, running a few analyzers quick out of curiosity, IBM X-Force and Pulsedive, show this IP has a bunch of malicious history associated with it. Due to the amount of indicators and details listed, I am simply putting a link to a TXT file with the raw API json output of just a couple analyzers.
There you have it, I might still do a full Wazuh write-up, but since there is so much good documentation on Wazuh's site, and in the community, I felt it wasn't really worth it. Please let me know otherwise!
God Bless
Dan


