Wazuh and Criminal IP Integration Howto

I am going to show you how to integrate Criminal IP's services in regards to enriching Wazuh IP address logs originating from the Internet. Criminal IP's API allows you to check IP address's and report back a variety of great information about that IP address. From its threat score and general reputation, if its a Tor exit node, VPN, Proxy, Cloud and or Hosting Provider and much more!
There will be two parts to the article, the howto section including a simple instructional on how to setup Criminal IP service into your Wazuh, and then the second will be a good demonstration of adding GeoIP location enrichment to the Criminal IP integration to then be able to plot the information on a World Map.
Getting Started
First thing you will need to do is go to https://www.criminalip.io/ to sign up for an API key. They do offer a free plan, but be forewarned it will not work at scale with what I am going to show you or in production. In my case, I subscribed to a plan that gave me 70,000 API call credits. In our case running close to 1000 endpoints in production at our MSP, this will eat up even that well before the month is over.
Once you signup, get your API key in your profile and write that down, as we will need to put that in the sample files you download below.
There is a few core files including python code, a rules file, and a code block you need to configure in your main ossec.conf file on your wazuh server. I do not take credit for making the code, I found it on Github. That being said, after not being able to get it to work for the life of me given the basic instructions from the author. I ended up using AI to check the code, and modified it to work with the newer versions of Wazuh. I am not sure if the author made a mistake in posting incorrect code or what, but it was almost there, just needed a few tweaks. I will make these available for download below at the following links. Go there and download each one before we get started.
Once you have downloaded these three files, open up the rules.xml file and modify the rule level of each rule based on your needs. In my example rules 12 and above I get email alerts globally so I tweaked them a little in this example. The numbers (blue arrow) can be changed from 1-15.
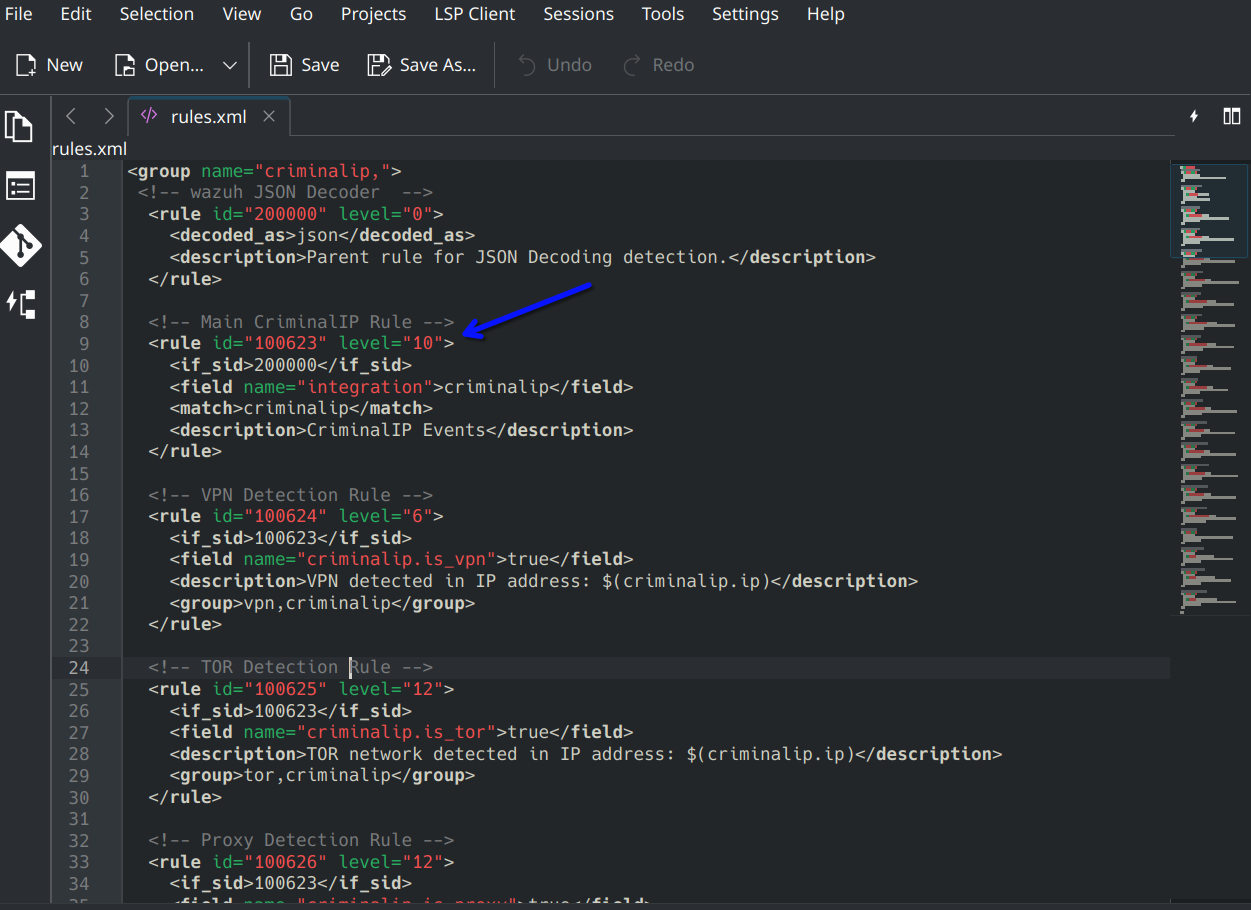
Once saved copy this rules file to your /var/ossec/etc/rules folder and change permissions to be like the other files for good measure. Do a ls -la on the folder and enter the following.
chown wazuh:wazuh rules.xmlThen make sure to chmod the file to match the others, if you are unsure you can always use the command:
stat --format '%a' <file>Next open up the custom-criminalip.py and at the top, paste your API key where it says "PASTE YOUR CRIMINAL IP API KEY HERE", then save the file.
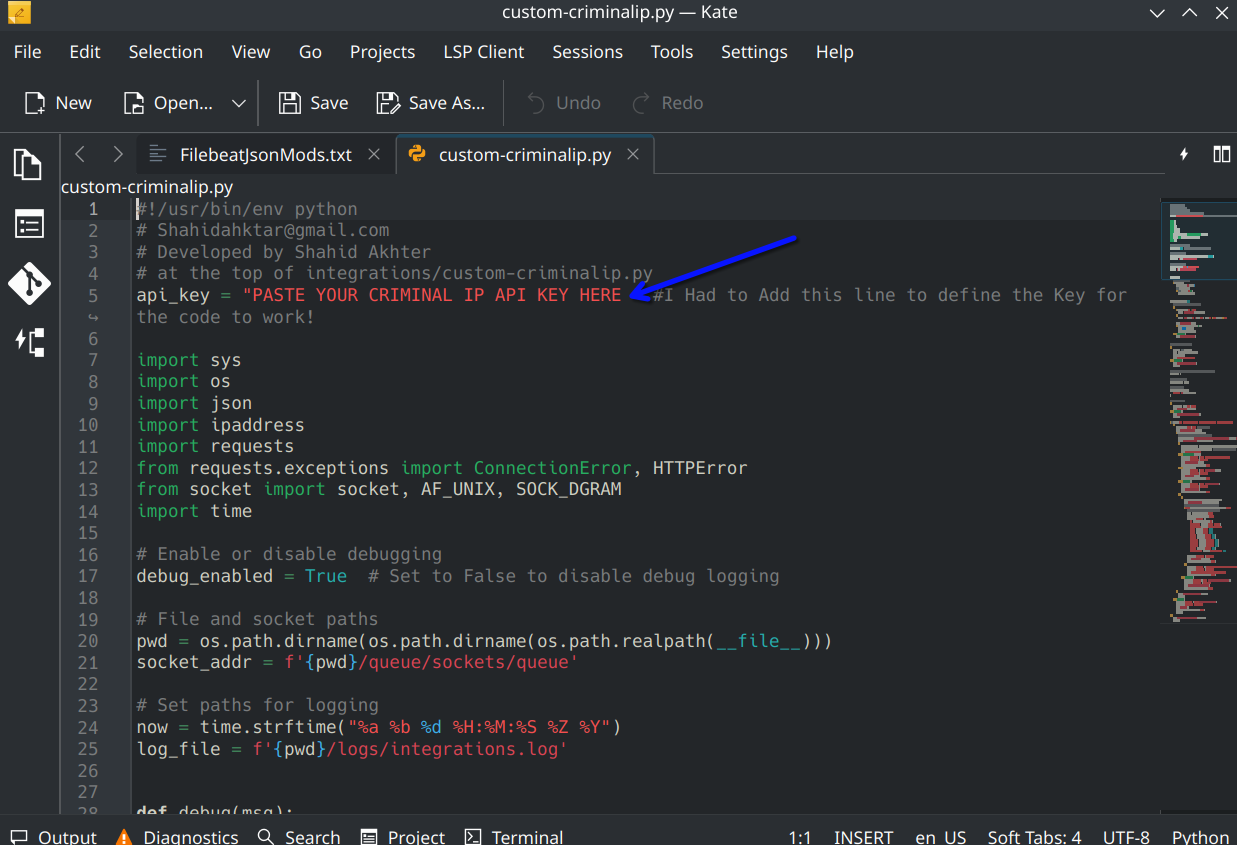
Now copy this file along with the custom-criminal file both into the integrations directory located at /var/ossec/integrations folder. Once again, check the owner and permissions of these files and make changes as necessary.
Next up we need to Insert the following into your ossec.conf file, located at /var/ossec/etc . First we will modify again by pasting the API key into the section where it says "PASTE YOUR CRIMINAL IP API KEY HERE".
<integration>
<name>custom-criminalip</name>
<api_key>PASTE YOUR CRIMINAL IP API KEY HERE</api_key>
<group>web, sshd, invalid_login, firewall, ids, system, database, application</group>
<alert_format>json</alert_format>
</integration>Save the file then we will need to restart the Wazuh Manager Service to activate the integration.
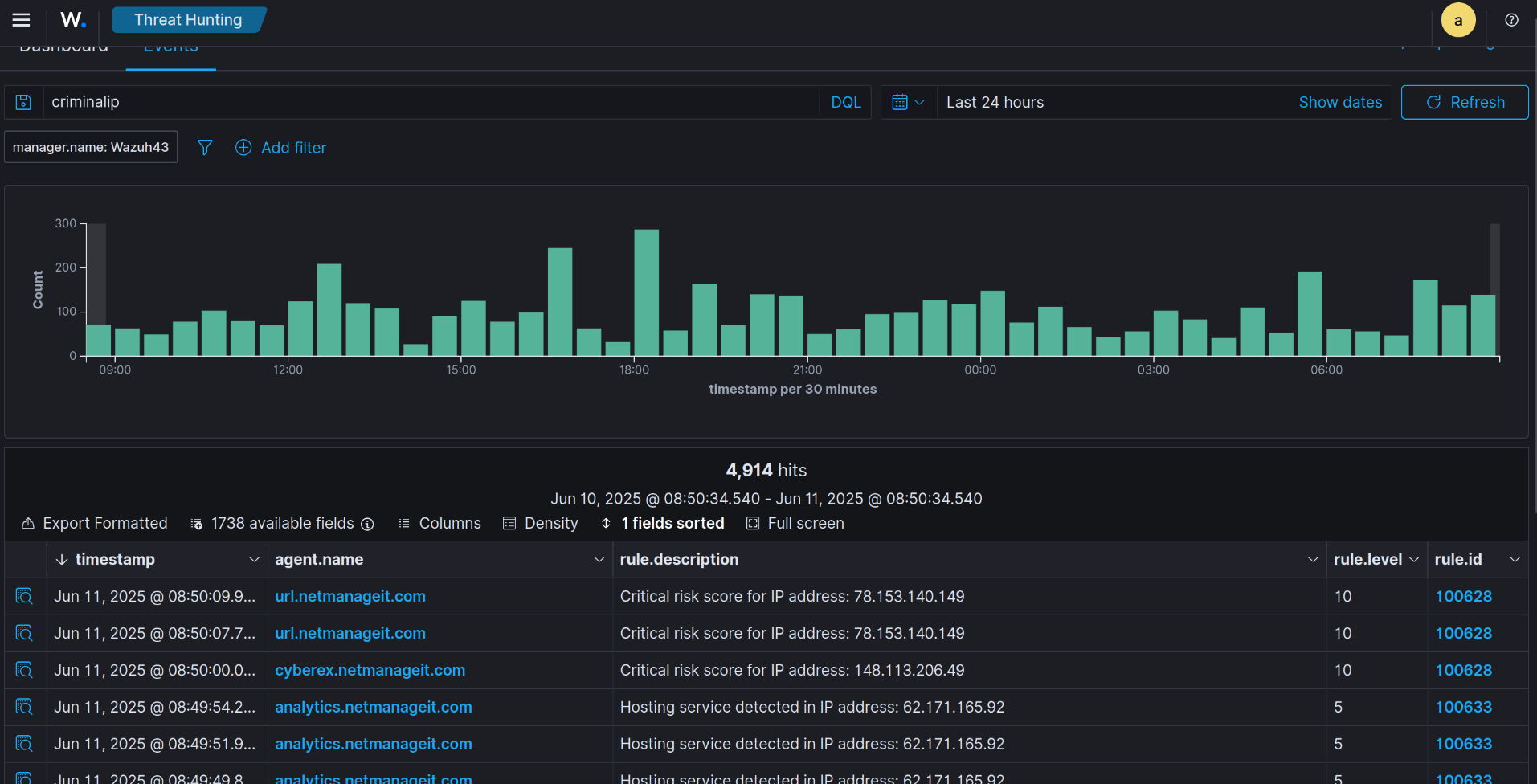
systemctl restart wazuh-managerGive it some time, and you can go to Threat Hunting and apply a filter for "criminalip" in events. Below is a ton for all my sub sites I host.
GeoIP Setup and Enrichment and World Map Demo
In the next section, I am going to show you how to make a world map, and enrich the index with Geo Location coordinates so the Criminalip enrichment can then be shown on the Map. Note, by default Wazuh won't enrich GeoIP and you will need to alter the filebeat JSON file so during ingestion it can insert coordinates lon & lat into the criminalip index entries.
Go to the usr/share/filebeat/module/wazuh/alerts/ingest directory and modify the pipeline.json file. Insert this code to match the other blocks.
{
"geoip": {
"field": "data.criminalip.ip",
"target_field": "GeoLocation",
"properties": ["city_name", "country_name", "region_name", "location"],
"ignore_missing": true,
"ignore_failure": true
}
},Save the file then run the following to refresh Filebeat.
filebeat setup --pipelinessystemctl restart filebeatWorld Map Demo
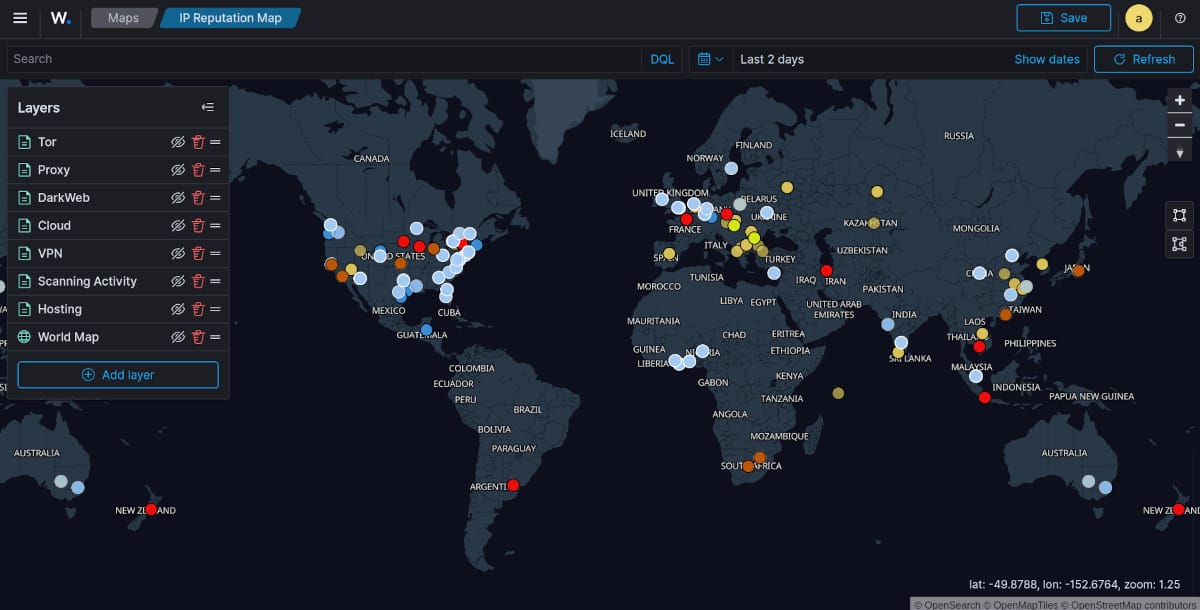
I made a quick map with multiple layers showing in 2 days what kind of connections and their general intention is shown in multiple screenshots below. I will not be going into how to create maps, as its outside the scope of this article. That being said, going to Visualize and create map from coordinates will get you started.
These map screenshots, show all the different types of IP address's constantly probing, scanning, attacking, fuzzing, checking vulnerabilities and mapping the Attack Surface. They are essentially trying to exploit and cause mischief with my other sites. There are about 12 in total.
NOTE : For clarification purposes here is a quick legend by colors
HOSTING - Blue / SCANNING ACTIVITY - yellow / VPN - red
CLOUD - light blue / PROXY - orange / TOR - neon yellow
Map of all Layers
Map of Hosting only
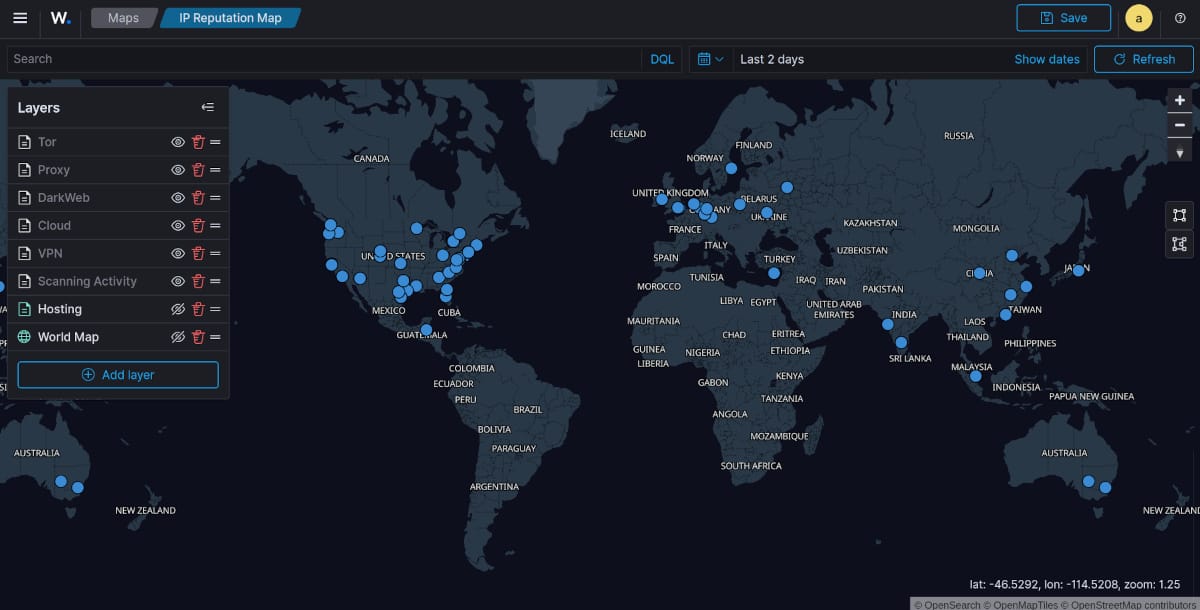
Map of Scanning Activity
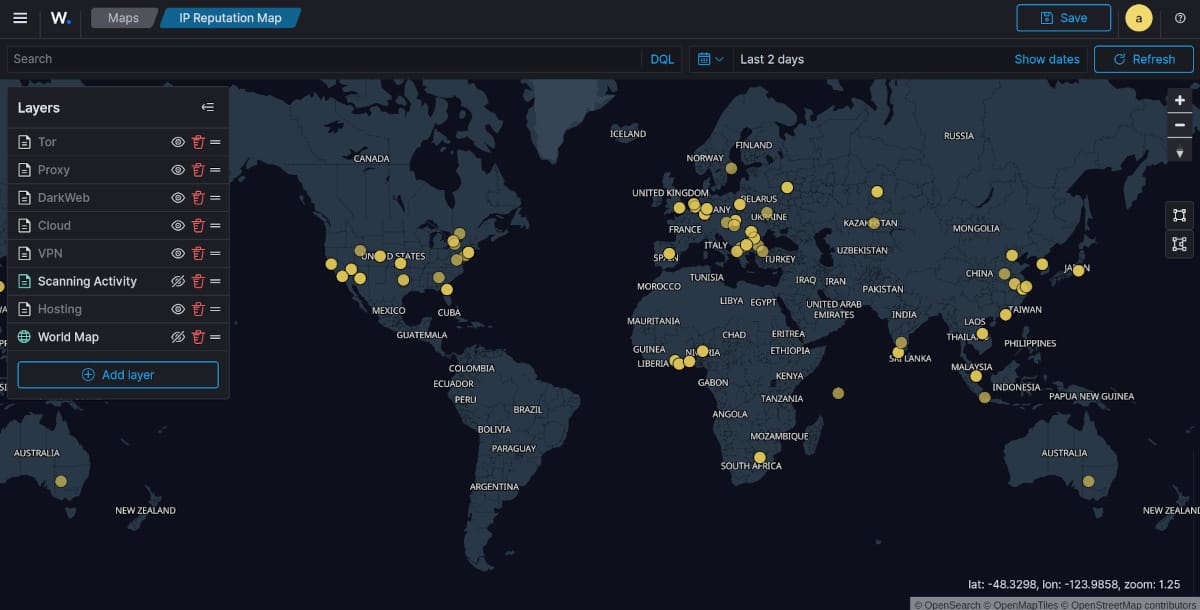
Map of Cloud Providers
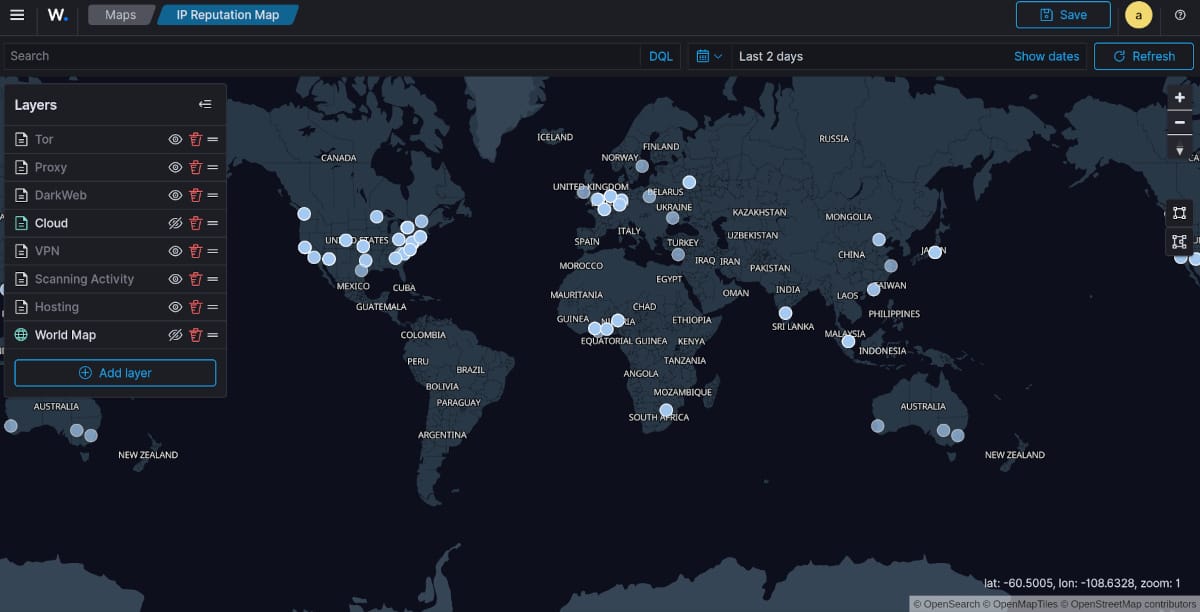
Map of VPN's
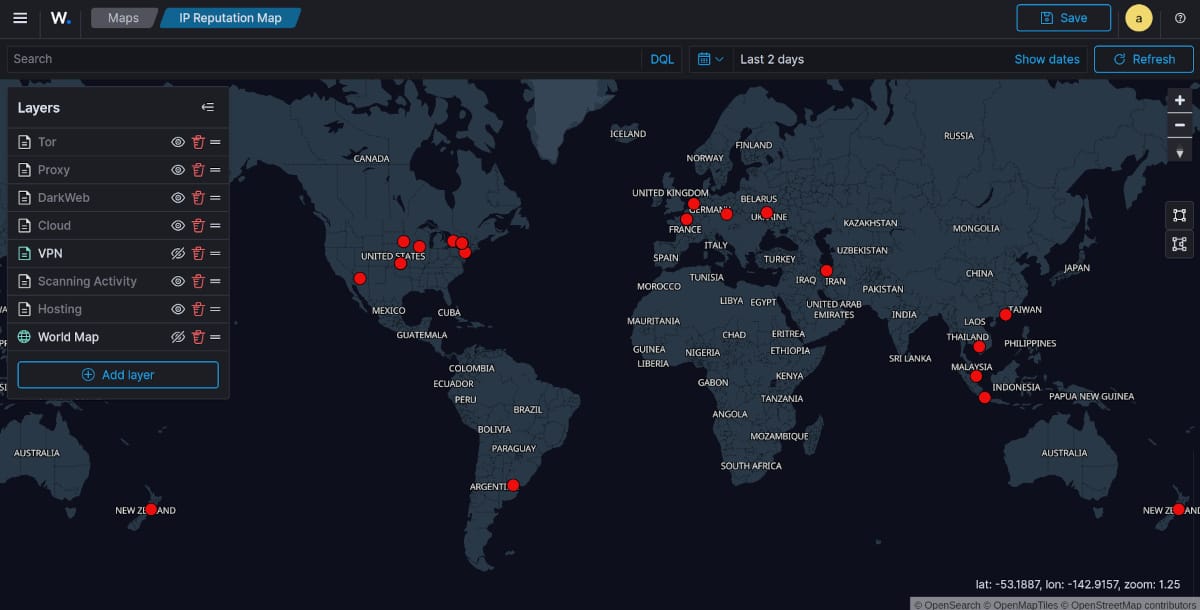
Map of Proxy's
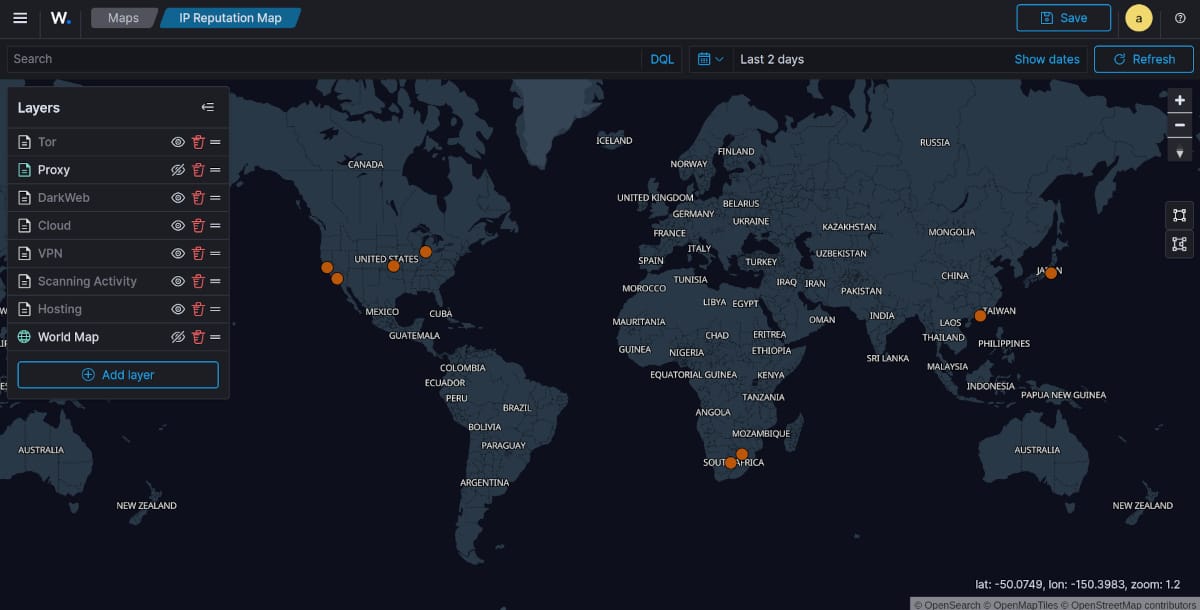
Map of Tor Nodes
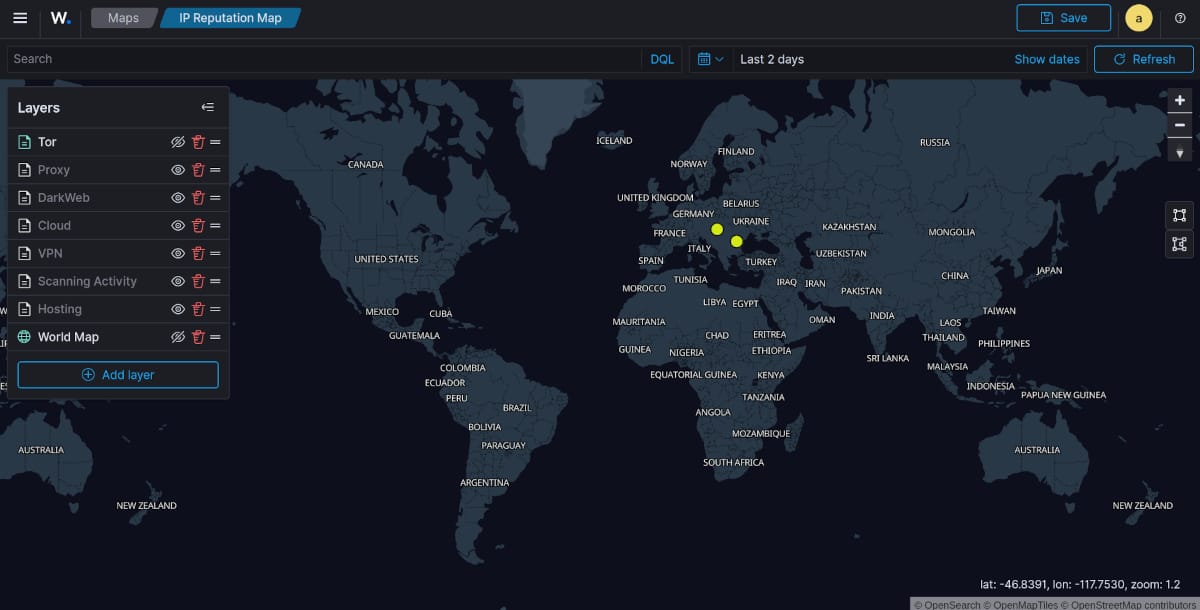
What is interesting to note, most of the classifications are IP's with "Scanning Activity". This layer when over laid on top of "Cloud" and "Hosting" clearly show, that most of the scanning activity is coming from VPS, Hosting and Cloud IP address blocks. Most often compromised servers or intentionally setup for this purpose to run 24x7 for the threat actors.
Hope you enjoyed this article, as usual if you find this useful, let me know, comment on LinkedIN etc.
God Bless
Dan


