.US Harbors Prolific Malicious Link Shortening Service
Krebs on Security
Click here for the article
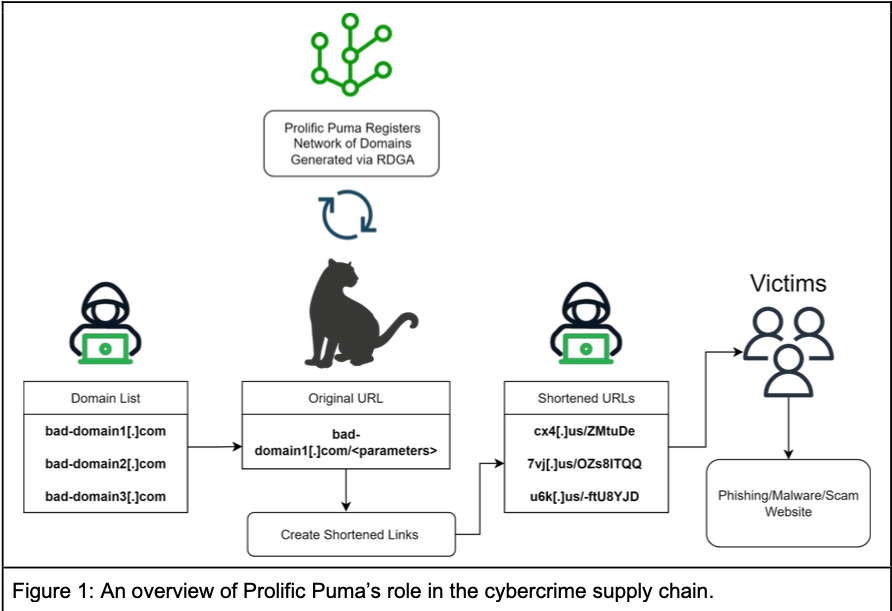
The top-level domain for the United States — .US — is home to thousands of newly-registered domains tied to a malicious link shortening service that facilitates malware and phishing scams, new research suggests. The findings come close on the heels of a report that identified .US domains as among the most prevalent in phishing attacks over the past year. Researchers at Infoblox say they’ve been tracking what appears to be a three-year-old link shortening service that is catering to phishers and malware purveyors. Infoblox found the domains involved are typically three to seven characters long, and hosted on bulletproof hosting providers that charge a premium to ignore any abuse or legal complaints. The short domains don’t host any content themselves, but are used to obfuscate the real address of landing pages that try to phish users or install malware. A graphic describing the operations of a malicious link shortening service that Infoblox has dubbed “Prolific Puma.” Infoblox says it’s unclear how the phishing and malware landing pages tied to this service are being initially promoted, although they suspect it is mainly through scams targeting people on their phones via SMS. A new report says the company mapped the contours of this link shortening service thanks in part to pseudo-random patterns in the short domains, which all appear on the surface to be a meaningless jumble of letters and numbers. “This came to our attention because we have systems that detect registrations that use domain name generation algorithms,” said Renee Burton , head of threat intelligence at Infoblox. “We have not found any legitimate content served through their shorteners.” Infoblox determined that until May 2023, domains ending in .info accounted for the bulk of new registrations tied to the malicious link shortening service. Since then, they found that whoever is responsible for running the service has used .US for approximately 55 percent of the total domains created, with several dozen new malicious .US domains registered daily. .US is overseen by the National Telecommunications and Information Administration (NTIA), an executive branch agency of the U.S. Department of Commerce . But Uncle Sam has long outsourced the management of .US to various private companies, which have gradually allowed the United States’s top-level domain to devolve into a cesspool of phishing activity. Or so concludes The Interisle Consulting Group , which gathers phishing data from multiple industry sources and publishes an annual report on the latest trends. As far back as 2018, Interisle found .US domains were the worst in the world for spam, botnet (attack infrastructure for DDOS etc.) and illicit or harmful content. Interisle’s newest study examined six million phishing reports between May 1, 2022 and April 30, 2023, and identified approximately 30,000 .US phishing domains. Interisle found significant numbers of .US domains were registered to attack some of the United States’ most prominent companies, including Bank of America, Amazon, Apple, AT&T, Citi, Comcast, Microsoft, Meta, and Target. Others were used to impersonate or attack U.S. government agencies. Under NTIA regulations, domain registrars processing .US domain registrations must take certain steps (PDF) to verify that those customers actually reside in the United States, or else own organizations based in the U.S. However, if one registers a .US domain through GoDaddy — the largest domain registrar and the current administrator of the .US contract — the way one “proves” their U.S. nexus is simply by choosing from one of three pre-selected affirmative responses. In an age when most domain registrars are automatically redacting customer information from publicly accessible registration records to avoid running afoul of European privacy laws, .US has remained something of an outlier because its charter specifies that all registration records be made public. However, Infoblox said it found more than 2,000 malicious link shortener domains ending in .US registered since October 2023 through NameSilo that have somehow subverted the transparency requirements for the usTLD and converted to private registrations. “Through our own experience with NameSilo, it is not possible to select private registration for domains in the usTLD through their interface,” Infoblox wrote. “And yet, it was done. Of the total domains with private records, over 99% were registered with NameSilo. At this time, we are not able to explain this behavior.” NameSilo has not yet responded to requests for comment. Experts who track domains associated with malware and phishing say even phony information supplied at registration is useful in identifying potentially malicious or phishous domains before they can be used for abuse. For example, when it was registered through NameSilo in July 2023, the domain 1ox[.]us — like thousands of others — listed its registrant as “Leila Puma ” at a street address in Poland, and the email address blackpumaoct33@ukr.net . But according to DomainTools.com , on Oct. 1, 2023 those records were redacted and hidden by NameSilo. This is why Infoblox refers to the people behind this malicious link shortening service as “Prolific Puma .” Infoblox notes that the username portion of the email address appears to be a reference to the song October 33 by the Black Pumas , an Austin, Texas based psychedelic soul band. The Black Pumas aren’t exactly a household name, but they did recently have a popular Youtube video that featured a cover of the Kinks song “Strangers,” which included an emotional visual narrative about Ukrainians seeking refuge from the Russian invasion, titled “Ukraine Strangers.” Also, Leila Puma’s email address is at a Ukrainian email provider. DomainTools shows that hundreds of other malicious domains tied to Prolific Puma previously were registered through NameCheap to a “Josef Bakhovsky” at a different street address in Poland. According to ancestry.com , the anglicized version of this surname — Bakovski — is the traditional name for someone from Bakowce, which is now known as Bakivtsi and is in Ukraine. This possible Polish and/or Ukrainian connection may or may not tell us something about the “who” behind this link shortening service, but those details are useful for identifying and grouping these malicious short domains. However, even this meager visibility into .US registration data is now under threat. The NTIA recently published a proposal that would allow registrars to redact all registrant data from WHOIS registration records for .US domains. A broad array of industry groups have filed comments opposing the proposed changes , saying they threaten to remove the last vestiges of accountability for a top-level domain that is already overrun with cybercrime activity. Infoblox’s Burton says Prolific Puma is remarkable because they’ve been able to facilitate malicious activities for years while going largely unnoticed by the security industry. “This exposes how persistent the criminal economy can be at a supply chain level,” Burton said. “We’re always looking at the end malware or phishing page, but what we’re finding here is that there’s this middle layer of DNS threat actors persisting for years without notice.” Infoblox’s full report on Prolific Puma is here .


