The case of the well crafted Phishing email.

Today I wanted to take you guys through a better than average phishing email that a customer received and requested we restore for them. The reason? "It is from a normal vendor who sends statements". How many times do we hear that? :)
So our Phishing platform caught it, as it does everything, because it is an incredible platform, but I won't plug them here in this blog post. In these cases where the user is positive its legit. I'll then go into the platform's native tools and dig out the headers and observables , while we take a secure preview of the link destination, in a safe sandbox environment, naturally. Tip: you can use KASM Workspaces for this, although I use a variety of tools for this portion of the analysis regardless.
Once I saw the URL sandbox landing page image, I knew immediately it smelled pretty bad. Here is the screenshot, can you see the clear red flags?
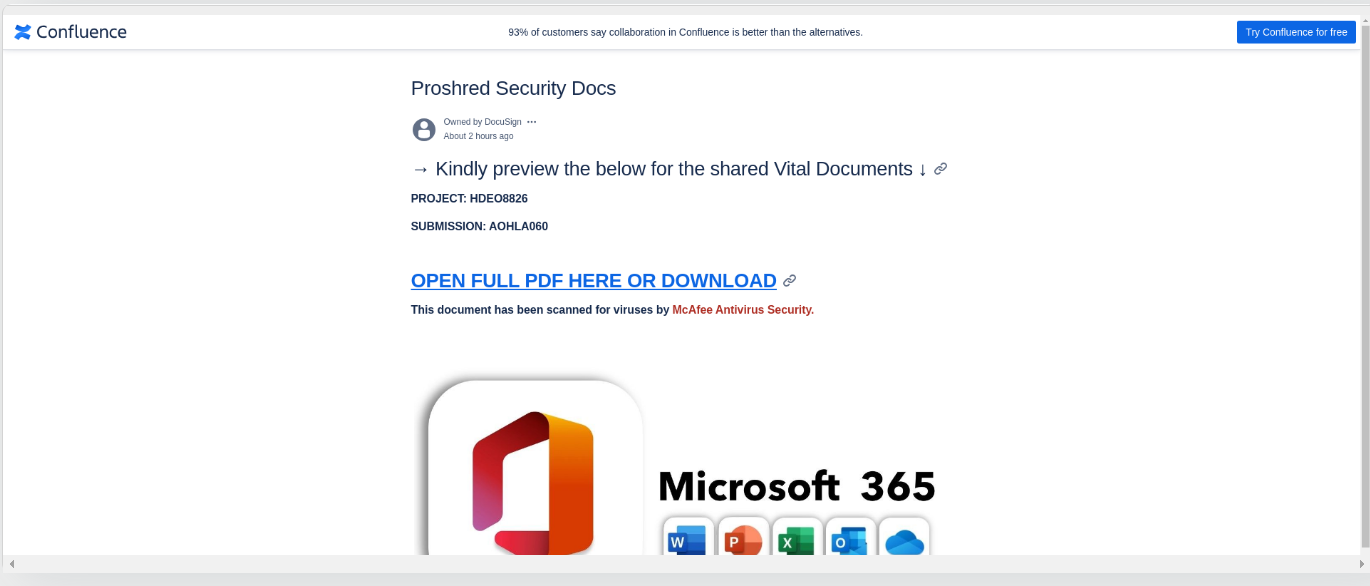
Ok... so first off, the Microsoft logos, right there in your face is a clear attempt to gain your trust. Did a good job with the images, but sized wrong, and then put a bold large text font above it "Microsoft 365", just looks unnatural. So then we move up a bit, and you see the bold blue capitalized link, there is the tempting call to action "click me, click me! Before the brain registers what you have just done. :) You will also notice an Atlassian logo upper left, again trying to gain trust. Finally, one last thing in red to drive it home, "Scanned for viruses by MCAFEE ANTIVIRUS". ok, now they are trying a little too hard. It was a good attempt, but we are only done looking at one piece of the evidence. At this point, this should give anyone pause, to further investigate.
So at this point, another thing I will do is copy the header information, and paste it in our public email header analyzer page at https://mha.netmanageit.com . This is a great quick tool, as it digests all the hard to look at text/code, and makes intelligence sense and lays it out to better find the things you are looking for. Anybody can do the same thing if they don't already use an email header analyzer they like. Here are the results after dumping the headers and clicking "analyze".
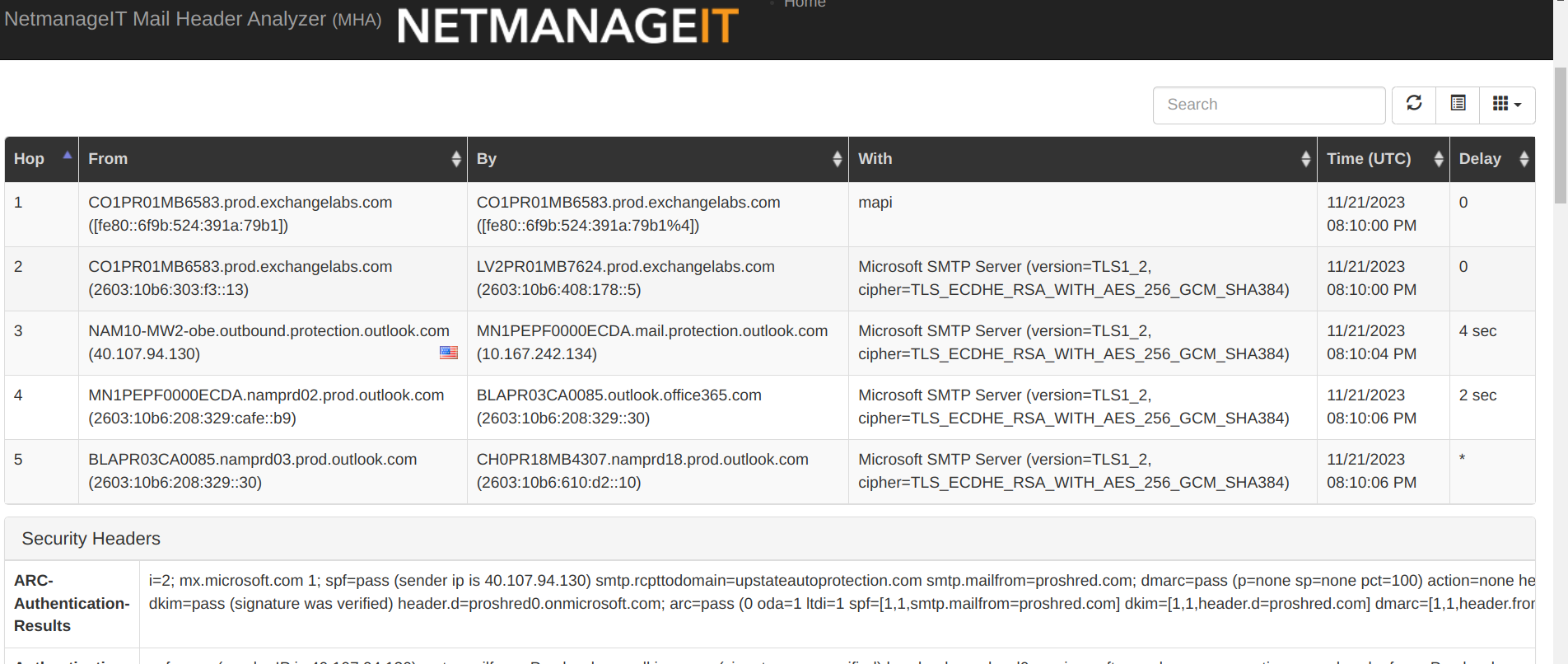
Now I am looking this over, and the first line caught my eye. Do you see it? The domain name of the first hop mail server address is "prod.exchangelabs.com". Ok, now that is pretty crafty... to disguise a source email domain name to look very "Microsoft", and blend in with all the other mail hops! So lets just use the word Exchange in there, it kinda works if your not looking close enough. Creative... I will give them that.
Now I am going to take that domain name, and the IP address and plug them in as observables in TheHive/Cortex to be checked ,which will run an additional 15-30 analyzers on it to see if anything obvious pops up. A few moments later it comes back with results. Surprisingly, not too many hits on obvious glaring problems, but one catches the eye. The orange, URLscan flags my attention. So you click and break it down further, and it indicates its a non existent domain. As in completely made up. Give them some points there for making it look similar to the other official mail hop naming schemes 365 uses. This is why it doesn't hurt to check it against many analyzers, if you only use a few, it could give you a false sense of security if they don't get a hit.
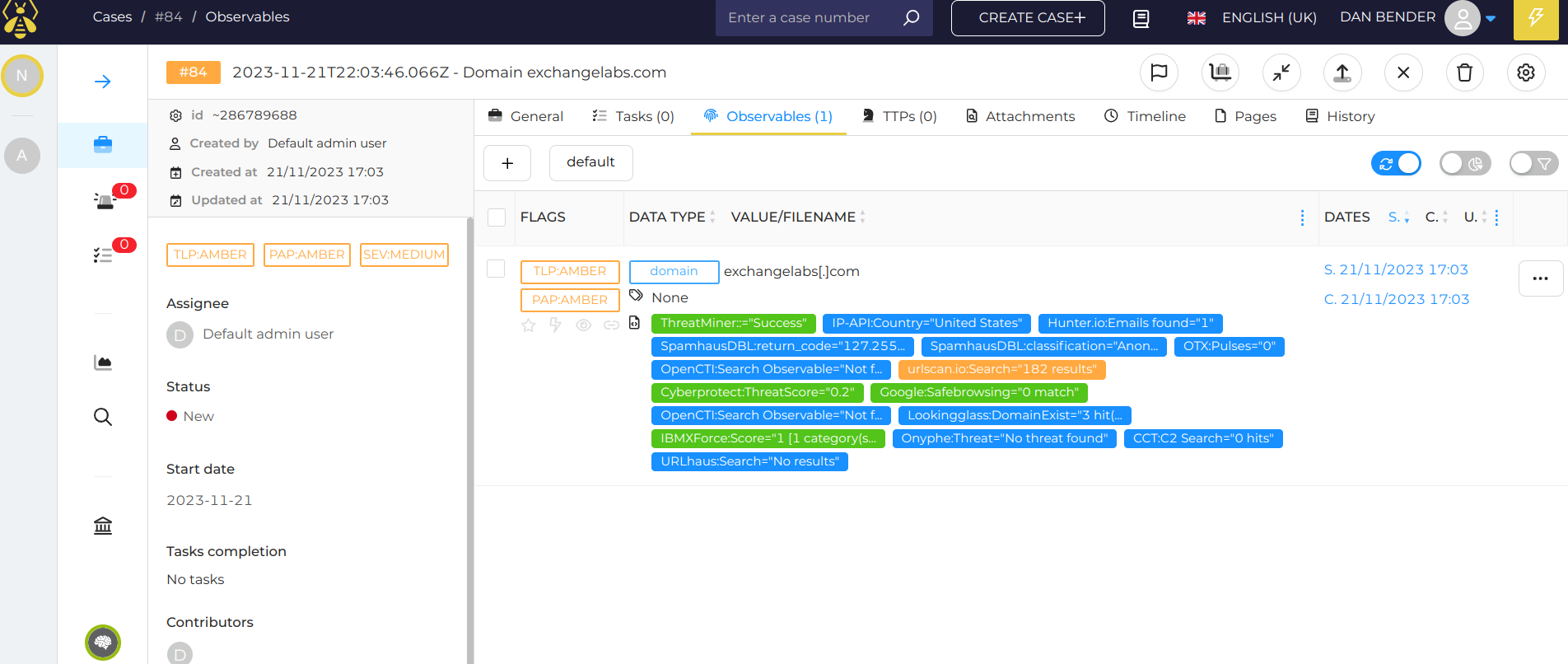
Now to be fair, the Anti-Phishing platform we use gives us a lot of this same information within their portal for further investigation. Although when your not 100% sure, you should always cross check things. In this case, with many different threat database sources, or as they call them in the TheHive/Cortex, Analyzers. Reaches out usually via API to a database and says, "hey you got anything that stinks on Mr. IP Address, Domain, File"?
So now, if your not completely confident at this point that we indeed have a malicious email on our hands after all we have seen so far. How about plugging in the observables in a few more platforms, in this case OpenCTI, or perhaps Alienvault. Ya know, just for fun and to give you that fuzzy feeling? :)
Gee, what do we have here?
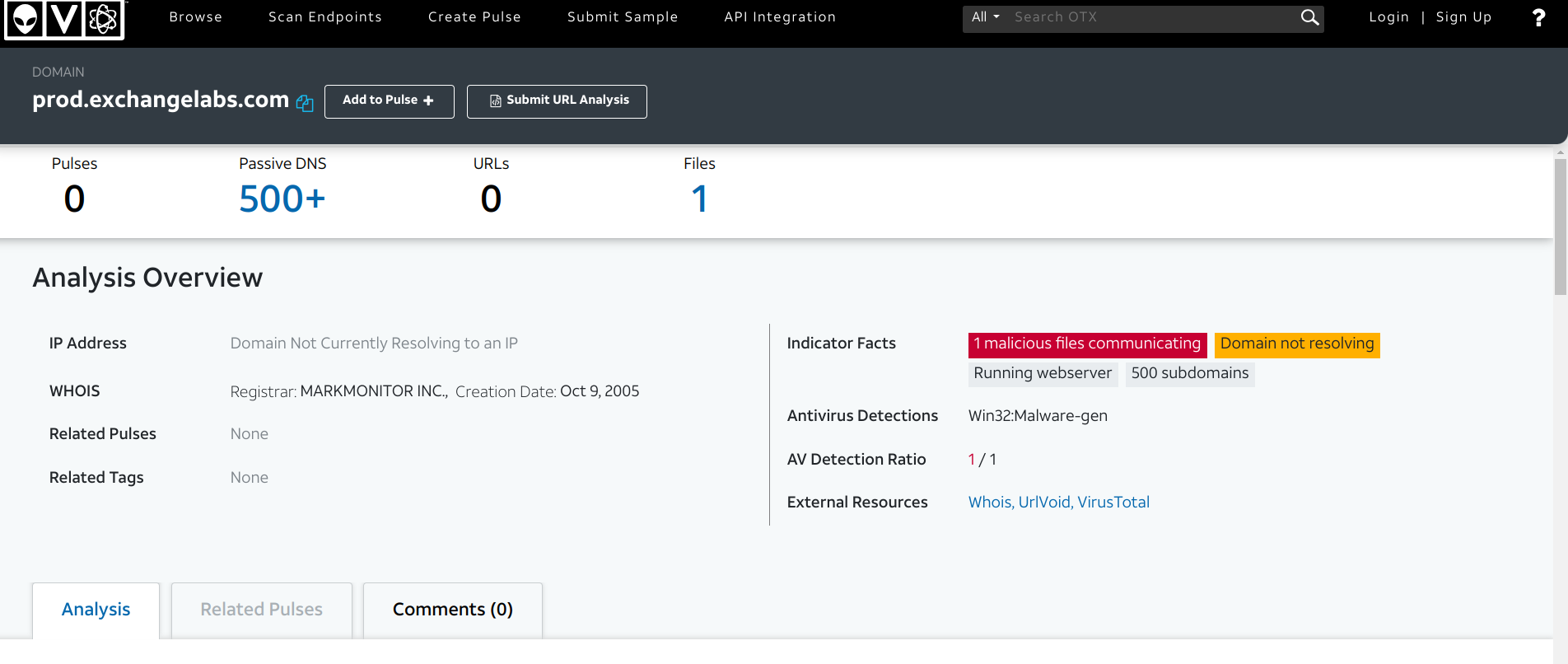
"Malicious files communicating and DOMAIN NOT RESOLVING".
There is that non existent domain thing again. So just add more correlation and evidence to the pile.
So in closing, a few points to finish up with. The Threat Actors may not have a certification or acronym after their names. They might not even be the best hacker or probably are even using tools, scripts and kits (phishing/RaaS) to run these campaigns.
What they do certainly have is a lot of time, and a lot of tenacity. Speaking as someone who has learned most of what I know from hands on, playing with, and trial and error since I was a young kid. These creeps are doing the same thing! So.... as we see, even with the best anti-phishing platform in existence, matched with the tools and experience to further analyze things under a microscope to really qualify if it was malicious or not. Normal users, or even average IT admins without training on this stuff, are sitting ducks.
Now the filters we use, did its job, and its right 99.9% of the time. It still stuns me how good it is compared to the competition. Cough..Cough I am looking at you Proofpoint, Mimecast, MS ATP, and lastly the dumpster fire of a company that once stood on top of the mail filtering kingdom, Barracuda. :) Oh, btw Microsoft marked it as CLEAN. Funny how so many admins all over the internet are complaining about MS filters quarantining truly legit emails left and right lately, yet the malicious ones just walk on by!
Make sure you put a buffer between your users or customers, do NOT let them self restore quarantined items. That is a fail safe, to allow the experts to really take a close look, and put human eyes on it and verify it one way or another. Once in a while, there are false positives, nothing is perfect, but that is why you have to use and learn these additional tools for further analysis and investigation. DO NOT leave anything to chance. One email like this slips through, due to your IT admin, MSP, or even Cyber Professional not trusting his gut, or trusting the person requesting the restore more than we should. This can potentially be catastrophic on so many levels. The email attack vector has been, and still is by FAR the most popular means how all these compromises starts. Good ol' social engineering. Do not put your guard down!
Be Safe
Dan


