KASM Workspaces Howto Installation and Usage
One of the cooler and less known tool and platform I use regularly, and has many uses for Cybersecurity professionals, Developers and learning purposes is KASM Workspaces.
What is it?
Kasm Workspaces is a docker container streaming platform that enables you to deliver browser-based access to desktops, applications, and web services. Kasm uses a modern DevOps approach for programmatic delivery of services via Containerized Desktop Infrastructure (CDI) technology to create on-demand, disposable, docker containers that are accessible via web browser. The rendering of the graphical-based containers is powered by the open-source project KasmVNC.
Kasm Workspaces was developed by a group of talented Cybersecurity professionals to meet the most demanding secure collaboration requirements that is highly scalable, customizable, and easy to maintain. Most importantly, Kasm provides a solution, rather than a service, so it is infinitely customizable to your unique requirements and includes a developer API so that it can be integrated with, rather than replace, your existing applications and workflows. Kasm can be deployed in the cloud (Public or Private), on-premise (Including Air-Gapped Networks), or in a hybrid configuration.
What can it be used for?
1. Secure and isolated Workspaces: Each user is assigned their own dedicated virtual workspace, ensuring that their activities and data are separate from others. This enhances security and privacy. This is great for learning Linux or playing around with products your not familiar with, or playing around with unknown or dangerous code and tools, think of a sandbox to play in.
2. Browser-based access: Users can access their virtual desktops and applications using a web browser, eliminating the need for complicated installations or configurations. It supports major browsers like Chrome, Firefox, and Edge.
3. Cross-platform compatibility: Kasm Workspaces can be accessed from various devices and operating systems, including Windows, macOS, Linux, Chrome OS, and mobile devices.
4. High performance: It utilizes GPU acceleration and advanced streaming technologies to deliver a responsive and smooth user experience, enabling resource-intensive applications to run seamlessly.
5. Collaboration features: Users can collaborate with teammates by securely sharing their virtual desktops or specific applications, facilitating real-time collaboration and workflows.
6. Security and compliance: Kasm Workspaces provides numerous security features, including network isolation, multi-factor authentication, encrypted data storage, and compliance with various industry standards.
7. Easy administration: Administrators can manage user access, deploy applications, monitor usage, and perform other administrative tasks through a centralized console.
Kasm Workspaces is particularly useful for organizations that require secure remote access to sensitive applications, need to manage virtual desktop environments, or aim to enhance productivity and collaboration among remote teams.
Two of the usages I think will be highly beneficial for using this platform are Cybersecurity folks and people learning Linux. For example, the security tools lets say in Kali/Parrot, or a self-isolated zero trust browser container for researching dangerous places of the DarkWeb or doing general OSINT and visiting malicious links for analysis in a safe sectioned off sandbox.
Installing KASM:
Installing KASM couldn't be easier. It's assumed you have one of the following flavors of Linux up to date and docker installed.
Ubuntu 18.04 / 20.04 / 22.04 (amd64/arm64) |
Debian 9 / 10 / 11 (amd64/arm64) |
CentOS 7 / 8 / 9 (amd64/arm64) |
Oracle Linux 7 / 8 / 9 (amd64/arm64) |
Raspberry Pi OS (Debian) 10 / 11 (arm64) |
The VM should have a min of 2vcpu and 4GB RAM, it is a pretty lightweight product, considering the capabilities it has. That being said, if you are going to have multiple users accessing the system, and keeping multiple sessions going at once, you will need more resources, just an FYI.
KASM provides a complete tarball file and an install.sh script that makes it a breeze to install. Use the following commands to install.
cd /tmp
curl -O https://kasm-static-content.s3.amazonaws.com/kasm_release_1.13.1.421524.tar.gz
tar -xf kasm_release_1.13.1.421524.tar.gz
sudo bash kasm_release/install.sh
Once its done installing, you will be given randomly generated and presented user and password at the end of the install process. Use these for initial access at the login page at https://SERVERNAMEORIP on port 443. You can then change your credentials how you see fit.

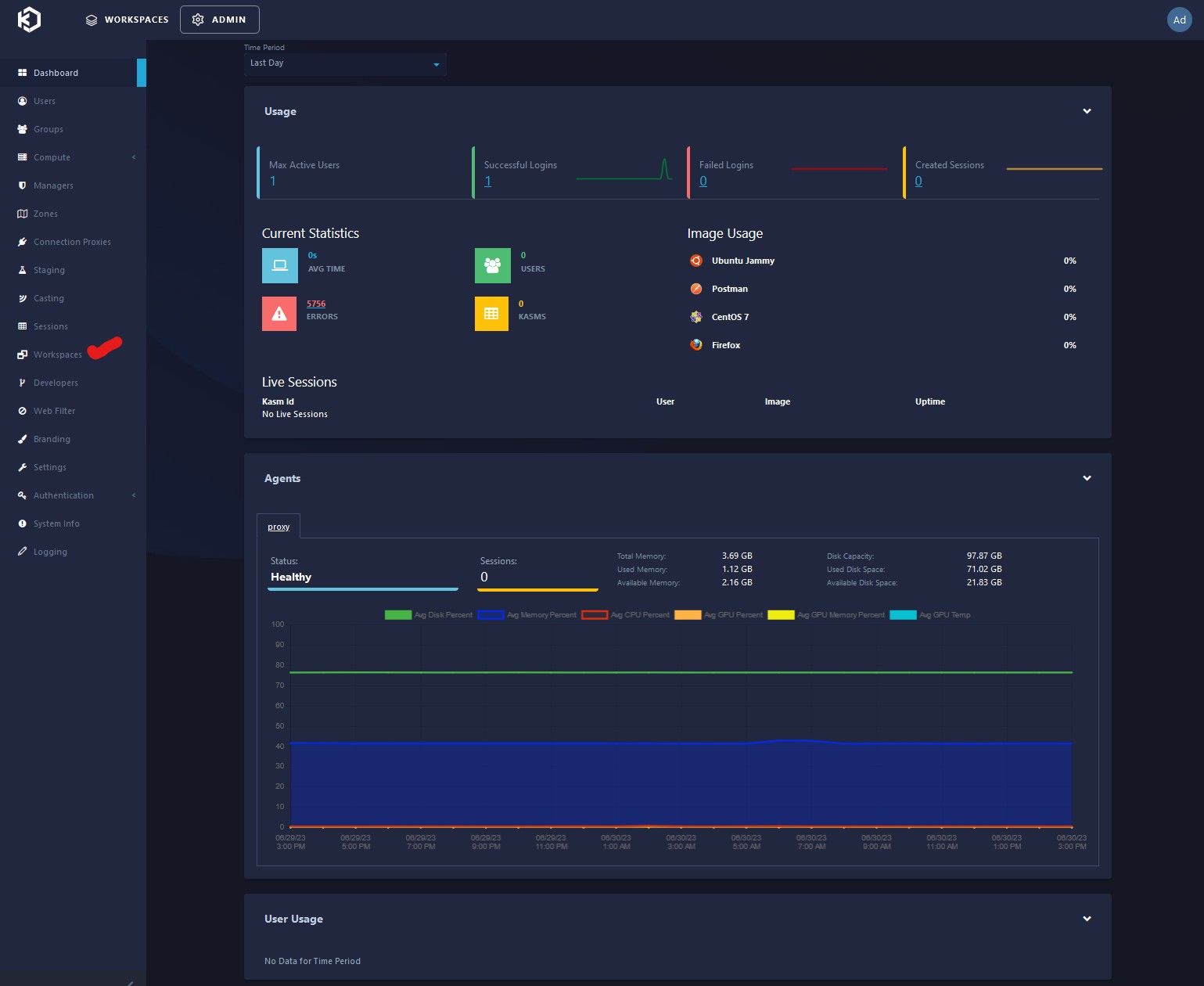
Once logged in, you be at the main Admin Dashboard, KASM is powerful and has alot of options to control the network stack, in terms of air-gapping, segmenting and controlling exactly what a workspace has access to. To get started with one of the more common area's you will be playing in, we will be looking at the
Workspaces option section. This controls which of the stock OEM created KASM images you want to enable and configure, as well as any custom images you create.
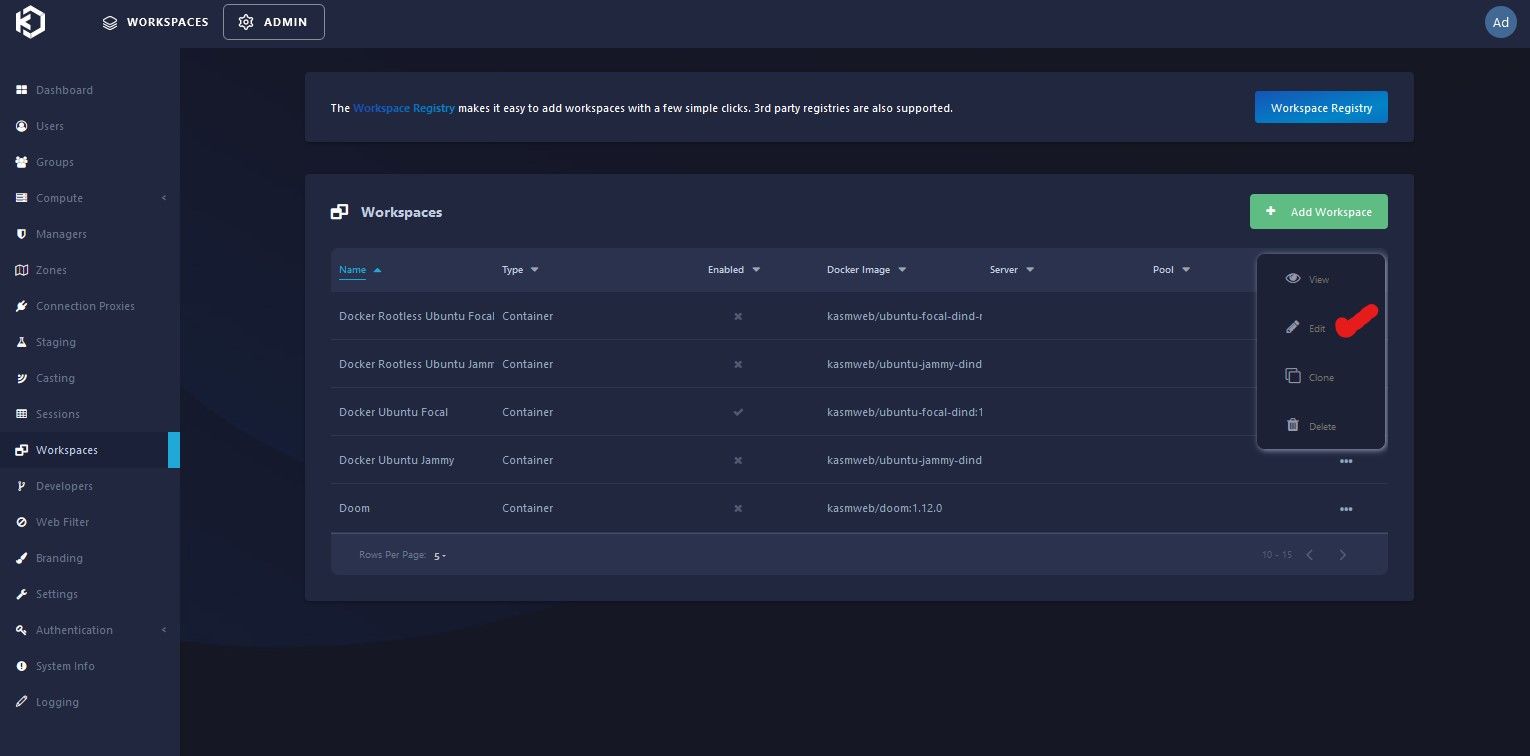
Clicking on Workspaces, brings up a list of built in KASM images ready to go, from Kali and other flavors of Linux OS's, Chrome and other browsers (browser isolation) etc. The ones enabled will have a check mark under enabled, ones that are not show an X. Enable one not already enabled, click on 3 dots to the right and click Edit.
Simply click on the "Enabled" checkbox to enable it in the user dashboard to be available for usage.
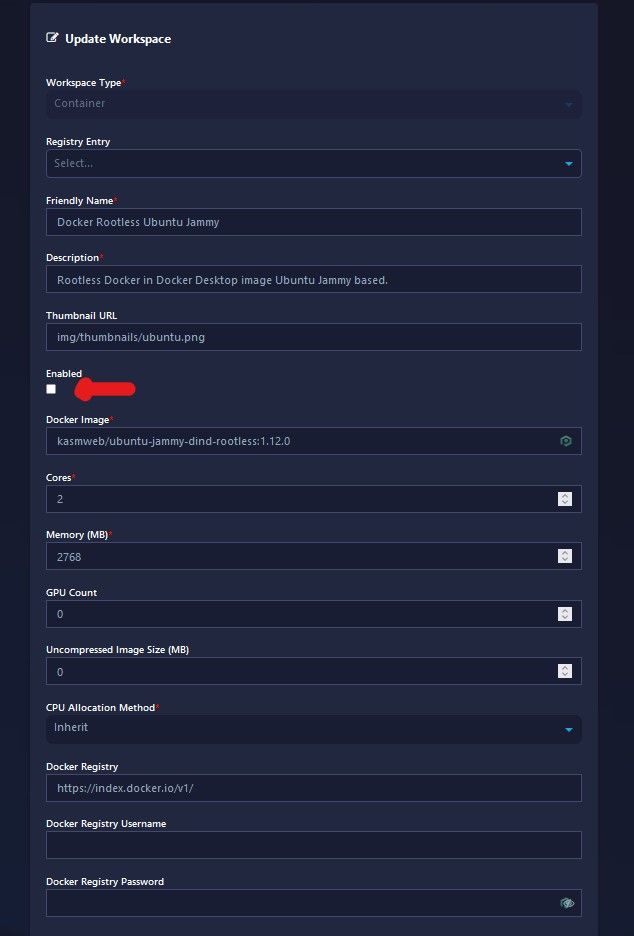
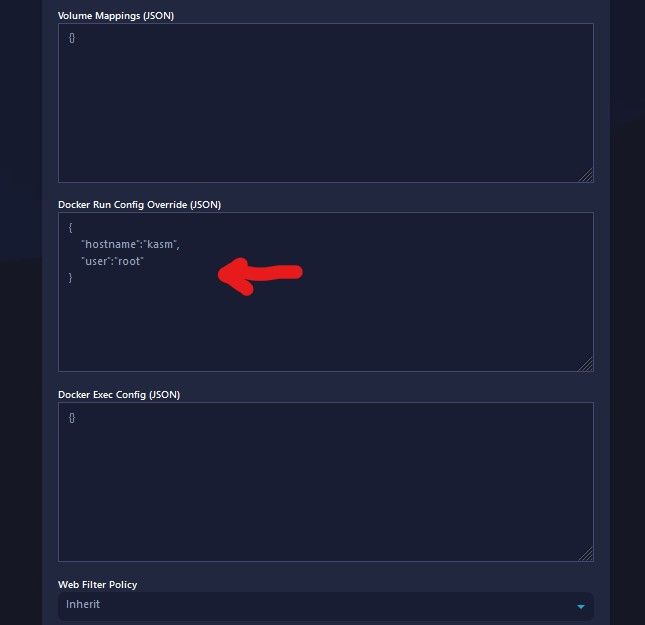
Note: Some of the options are self-explanatory, and can be referenced in the documentation, I will post the link to the official documentation at the end of article. One of those options I want to make you aware of is how to make root level access available to an image you enabled or a custom image you create yourself that does has not already been pre-configured with root level privileges.
Go to "Docker Run Config Override" field and include the following "user":"root" see screenshot. When your done with settings, just click "Submit" to save changes.
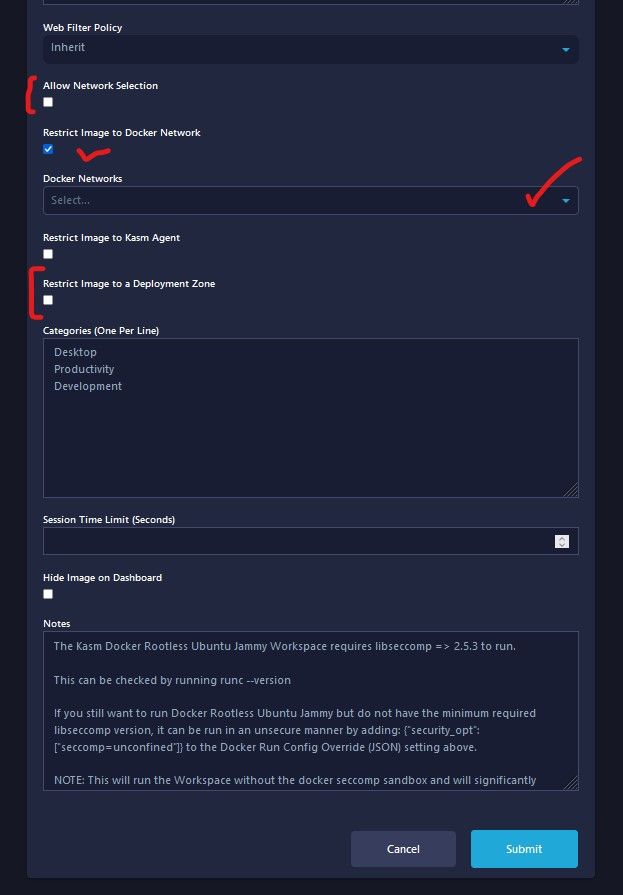
Next is the options for Network selection, you can Restrict Image to the Docker Network, or allow the user to pick a network with the "Allow Network Selection", or restrict them to a deployment zone.
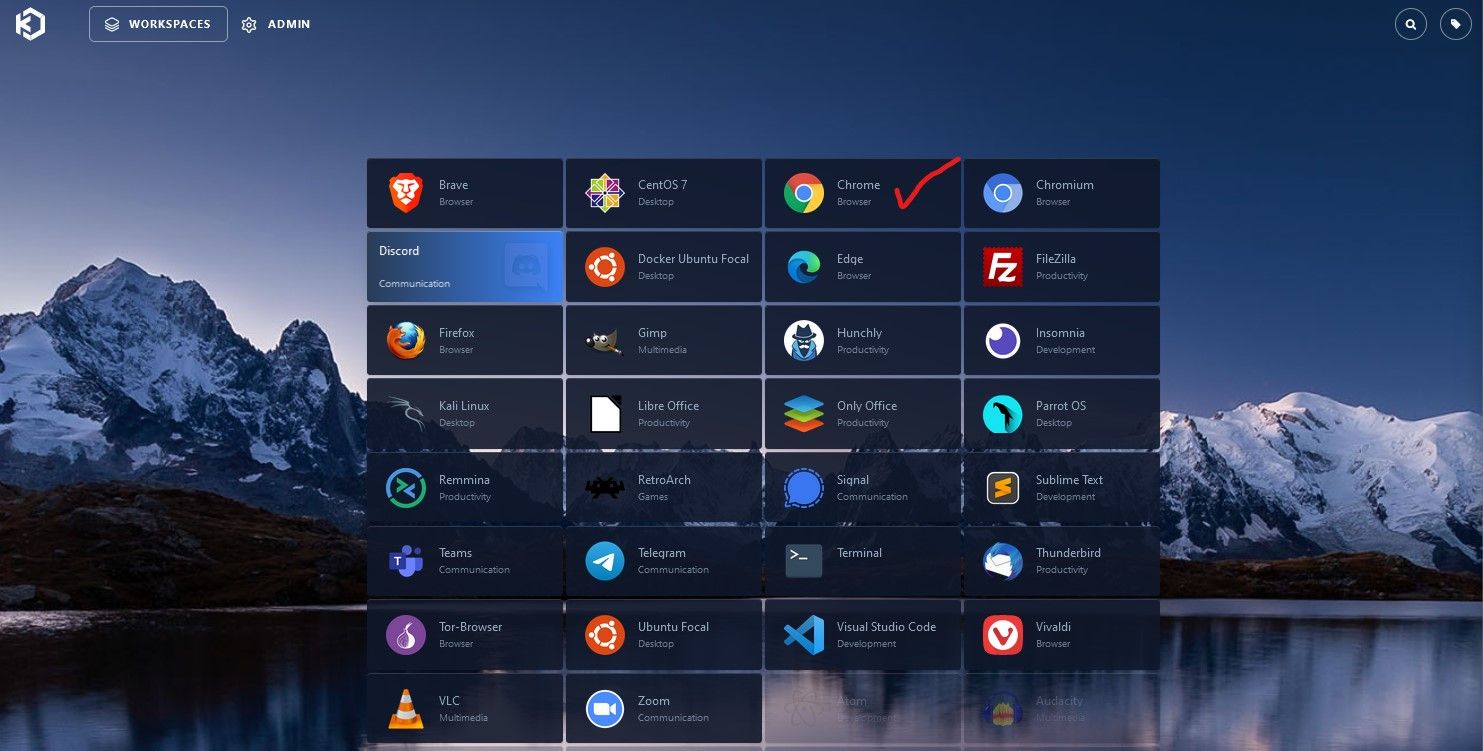
Using KASM:
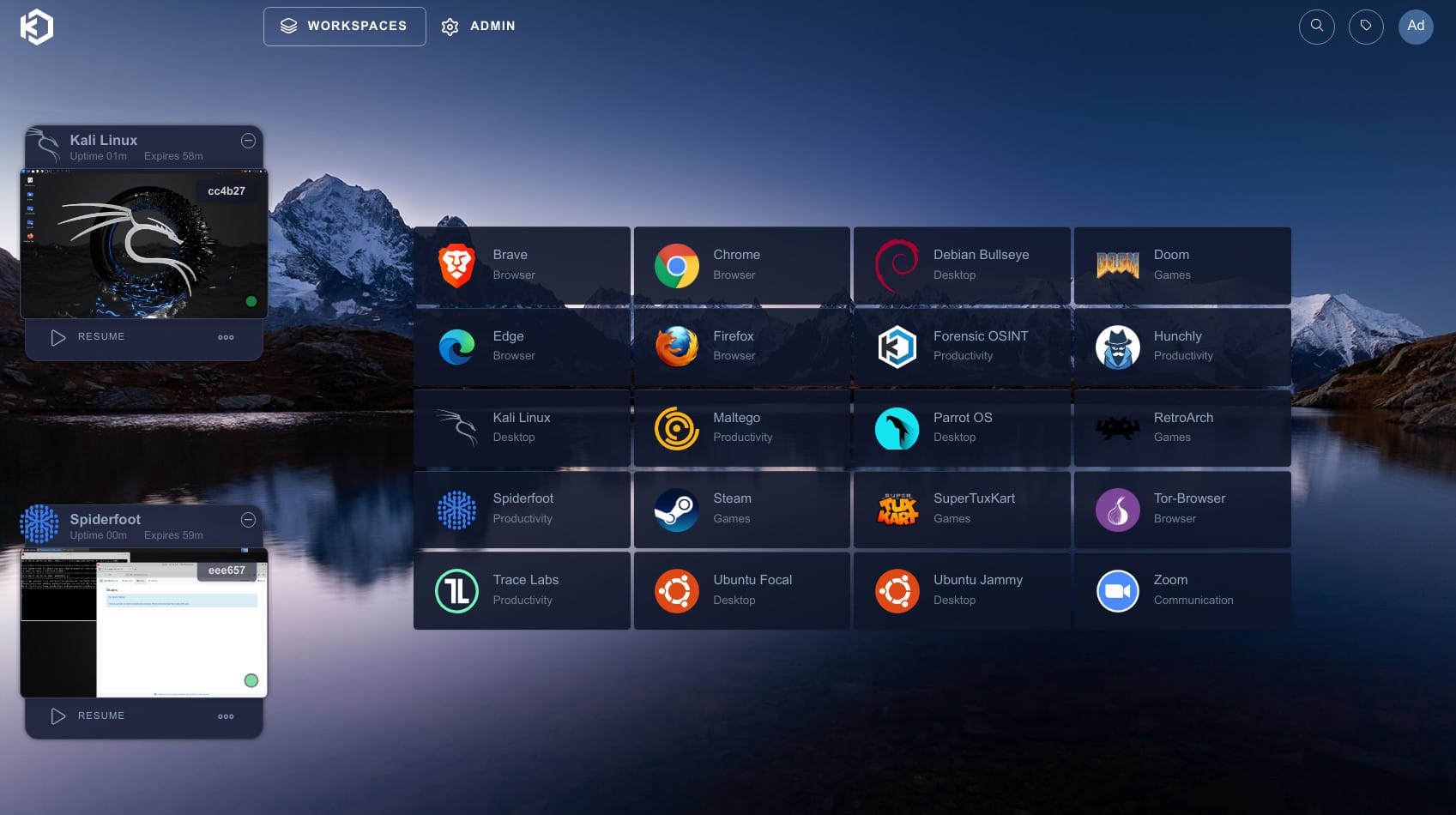
When clicking on the "Workspaces" main button on the top next to "Admin" button you are presented with the Available Workspaces dashboard screen. Lets Spin up a Chrome Isolate Browser Sandbox, for example testing malicious link for forensics.
Click Session, and almost immediately you will notice a browser within your browser. Notice the PopOut sidebar, this is where to control your interaction with the container and clipboard etc. Click on the right arrow to pop it out for options during usage. Notice the options are pretty self explanatory and similar to what you might find with a remote access tool like Anydesk, Teamviewer etc.

You can leave a session open, or delete the session instantly by clicking the available options. If you choose to leave it open and go back you will see its still running in the background, and will be listed as a tab. Click 3 dots to delete, or click resume etc. If you are going to have multiple users and sessions open, you will naturally need more RAM set for your KASM VM.
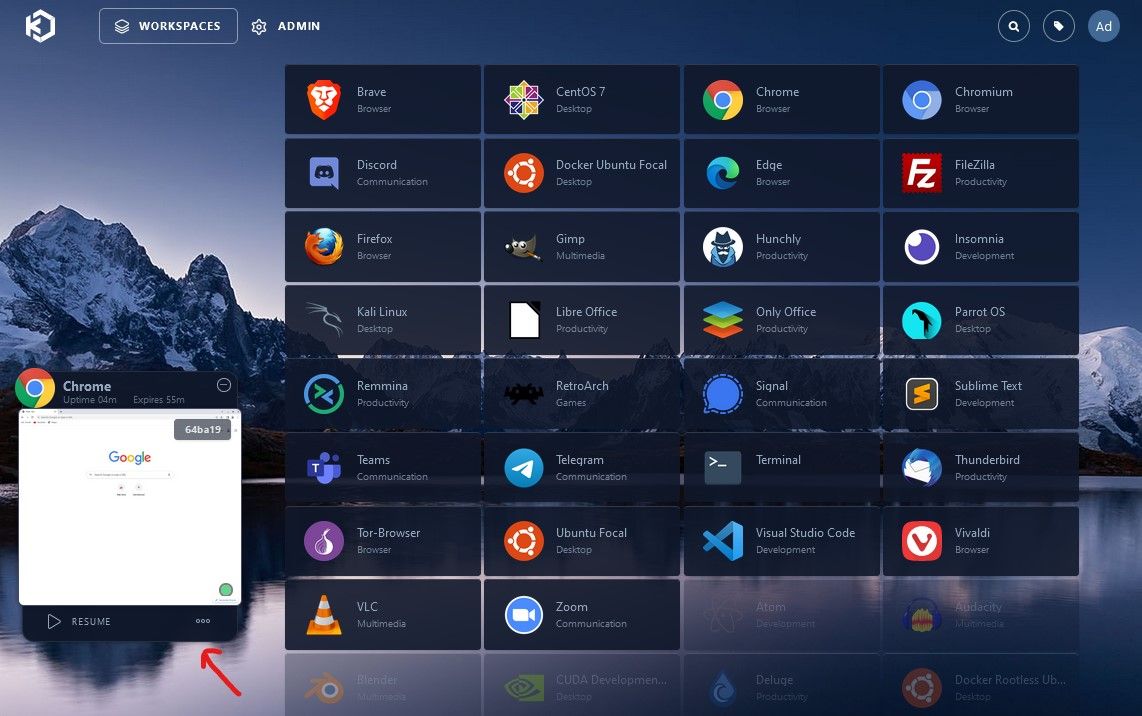
Now lets spin up a Kali Linux container for learning and using the OS and tools included. Click on Kali, if you like Parrot, that is included as an OEM image as well.
It took all of 4-5 seconds after clicking Launch for Kali to show the desktop ready to go, again notice that same side bar pop out. This platform is so quick, its stunning.
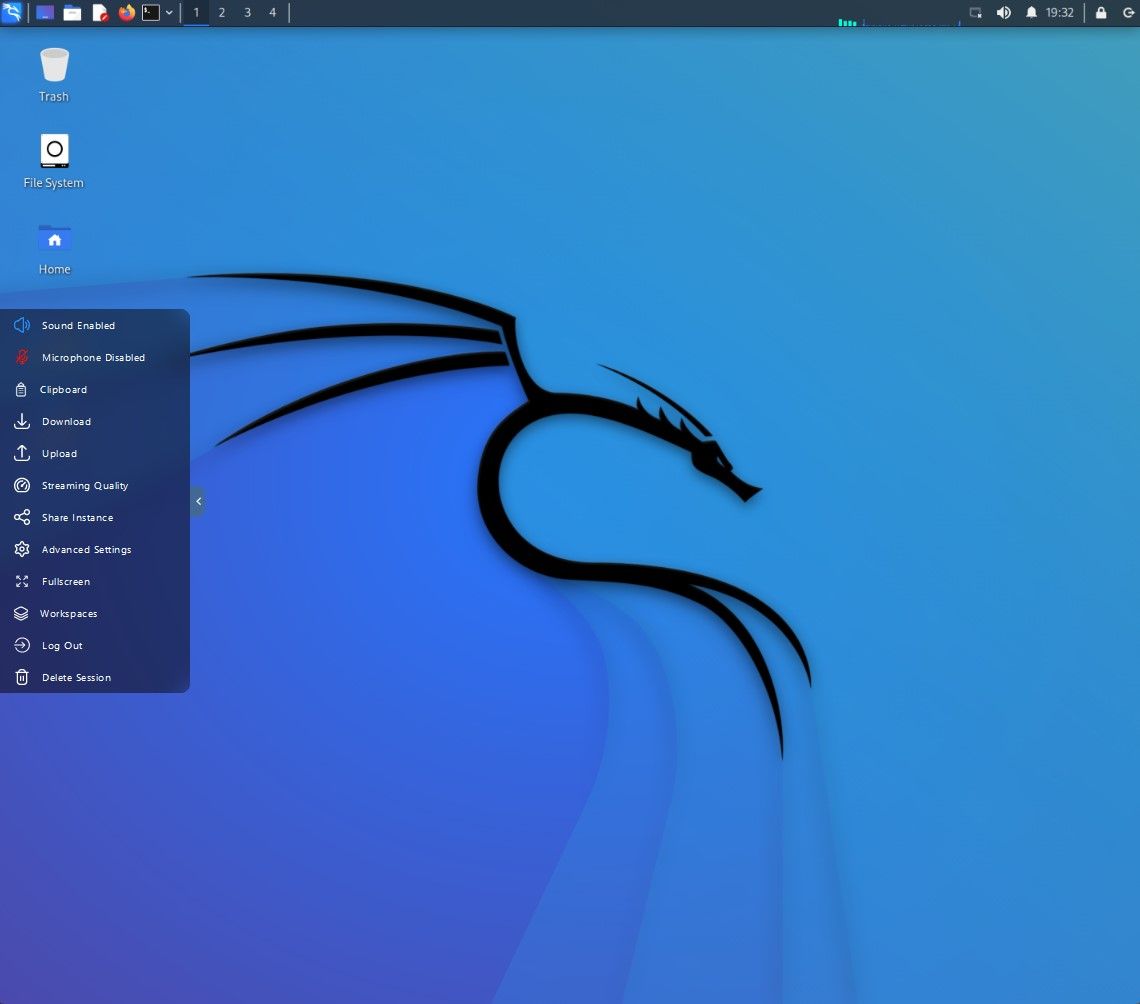
This is wonderful for learning Linux and Pen Testing/Security, with specific Linux distros. If you screw something up, you can in seconds, delete and start over! Super cool!
I hope you enjoyed this mini tutorial, and how it can be a great tool if your a Developer, Cybersecurity Professional, or just someone wanting to learn Linux and Open Source software.
The official KASM documentation can be found here:
Till next time! Of course if you like these articles, please share!
Dan



