How Attackers Can Own a Business Without Touching the Endpoint
TheHackerNews
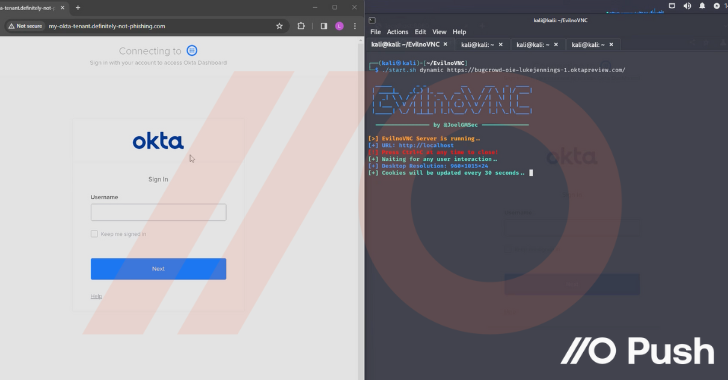
How attackers are hacking organizations without touching the endpoint by targeting cloud identities.

TheHackerNews

How attackers are hacking organizations without touching the endpoint by targeting cloud identities.